Best Secure Collaboration Tools in 2026

Collaboration fuels the engine of modern work, turning scattered teams into synchronized networks of productivity. Messages move in seconds, video calls bridge continents, documents evolve in real time, and projects advance across digital platforms. This constant flow keeps organizations agile and connected, yet every new connection widens the doorway for risk. Security no longer lingers in the background — it stands at the center of collaboration’s promise.
As remote and hybrid work reshape daily operations, the stakes climb higher. Protecting data, meeting compliance requirements, and fending off cyberattacks have become non-negotiable. A platform that ignores these safeguards does more than slow progress; it leaves the vault unlocked. Sensitive business details slip into the wrong hands, trust erodes, and vulnerabilities invite threats that can shake an entire organization.
In fact, this worldwide remote workforce security industry was estimated near USD 56.15 billion during 2024, and it is expected to expand by more than 21% each year until 2030.
As organizations step toward 2026, companies continue requiring additional features within their collaboration solutions: full-scale encryption, data residency, detailed permission controls, and effortless integration across enterprise IT networks. Whether operating as a startup protecting customer interactions or as a multinational corporation functioning under rigorous compliance standards, selecting an appropriate secure collaboration platform remains essential.
What are Secure Collaboration Tools, and Why do You Need Them?
Secure collaboration platforms represent digital systems created to assist groups in exchanging messages, distributing files, and overseeing projects while guaranteeing sensitive details stay safeguarded. Unlike typical collaboration software, these offerings maintain a heavy focus on protection and governance, rendering them vital for enterprises managing private information or functioning within controlled sectors.
Why Should You Care?
Secure collaboration systems function as digital environments developed to support teams in exchanging messages, transferring documents, and directing projects while ensuring sensitive information remains shielded. Unlike ordinary collaboration software, these platforms emphasize strong defense and regulatory adherence, making them indispensable for companies dealing with confidential records or working within tightly monitored industries.
Consider everything a team distributes daily: strategy presentations, customer records, financial analyses, or confidential conversations regarding upcoming agreements. For insiders, this may appear as routine business. For outsiders, however, it becomes a valuable treasure trove.
Hackers, competitors, or even disgruntled insiders could all target such information, deploying tactics ranging from social engineering to malicious payloads in cybersecurity attacks. A single intercepted meeting might disclose private negotiations. An unintentionally shared file could uncover critical pricing plans. Once data escapes, the consequences can prove lasting, spanning lost profits to diminished trust.
Picture this scenario: a sales division presents to a significant client via online conference. Without proper protection, an intruder intercepts the exchange and captures the proposal. Soon after, a competitor approaches with nearly identical terms, and the anticipated contract disappears.
Secure collaboration networks function like resilient bastions shielding today’s dangers. Equipped through robust encryption, granular access policies, and regulation-focused protections, they guarantee each dialogue remains restricted to individuals who qualify. Inside this safeguarded environment, groups share insights openly, construct with assurance, and direct their efforts toward creativity and progress — all absent the intrusion of unwelcome listeners slowing their drive.
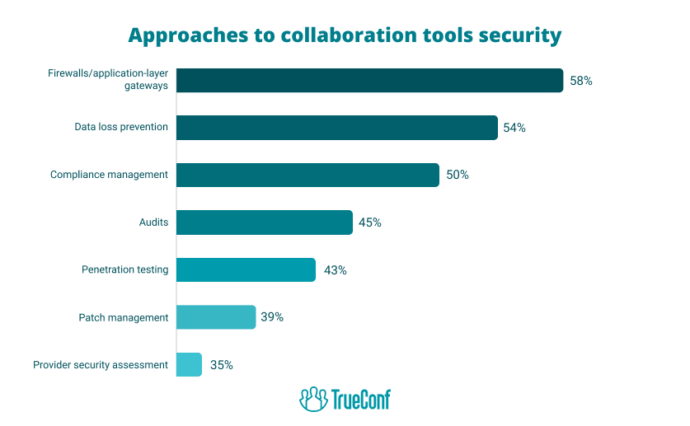
The Core Features to Look for In a Secure Collaboration Software
End-to-End Encryption
End-to-end encryption (E2EE) acts as a digital lockbox, ensuring that only the sender and the chosen recipient can unlock the contents of messages, calls, or shared files — but you still need to measure performance through defined test metrics to validate its effectiveness. Even when traffic flows through third-party servers, no outsider — not even the platform provider — can pry it open. This principle forms the cornerstone of confidential and trustworthy collaboration in a digital-first world.
Data Loss Prevention
Data Loss Prevention (DLP) serves as a vigilant guardian over sensitive information. It monitors how data moves, flags risky behavior such as sending confidential files outside company walls, and enforces policies that keep knowledge tightly secured. For organizations, DLP delivers peace of mind: employees collaborate freely, knowing their actions won’t put critical assets at risk.
Multi-Factor Authentication
Passwords alone are fragile shields against phishing, brute-force attempts, or careless reuse. Multi-factor authentication (MFA) fortifies defenses by adding extra checkpoints — whether a code sent to a mobile device, a fingerprint scan, or a hardware token. With this layered protection, MFA drastically reduces the likelihood of unauthorized logins and hostile account takeovers.
Data Compliance and Privacy Standards
Enterprises now confront rigorous compliance structures including GDPR, HIPAA, and ISO/IEC 27001. A trusted platform does not merely align with such regulations — it illustrates accountability using audit records, delivers adaptability in storage locations, and integrates confidentiality throughout its foundation. Compliance represents beyond a formal requirement; it stands as a tangible pledge to associates and clients that their information is managed with the utmost degree of diligence.
Top 10 Secure Collaboration Tools in 2026
|
Software |
Key Features |
Security |
|---|---|---|
|
TrueConf |
Video conferencing, team chat, webinars, hybrid/on-premises deployment |
End-to-end encryption, MFA, GDPR/HIPAA compliance, on-premises hosting |
|
Asana |
Task/project management, workflow automation, dashboards |
SSO, MFA, role-based access, GDPR/SOC 2/ISO 27001 compliance |
|
Trello |
Boards, lists, cards for task tracking, Power-Ups integrations |
2FA, SSO, GDPR/SOC 2 compliance, encryption in transit/at rest |
Zoom |
Video meetings, webinars, chat, cloud telephony |
End-to-end encryption (optional), MFA, GDPR/HIPAA/SOC 2 compliance |
|
Microsoft Teams |
Chat, video meetings, file sharing, deep MS 365 integration |
Encryption at rest/in transit, MFA, GDPR/HIPAA/ISO compliance |
Zoom |
Video meetings, webinars, chat, cloud telephony |
End-to-end encryption (optional), MFA, GDPR/HIPAA/SOC 2 compliance |
|
Google Meet |
Browser-based video meetings, real-time captions, Google Workspace integration |
Encryption in transit, MFA/SSO, GDPR/HIPAA compliance |
ClickUp |
All-in-one tasks, docs, chat, goals, dashboards |
SSO, 2FA, SOC 2 compliance, GDPR readiness |
|
Flock |
Team chat, video calls, task management, polls |
2FA, SSO, GDPR/SOC 2 compliance, encryption at rest/in transit |
Wire |
Secure messaging, voice/video calls, file sharing, open-source |
Default E2EE, on-premises option, GDPR compliance, IAM integration |
|
Google Drive |
Cloud storage, real-time document collaboration, Workspace integration. |
Encryption at rest/in transit, DLP, MFA, GDPR/HIPAA/SOC 2 compliance. |
1. TrueConf
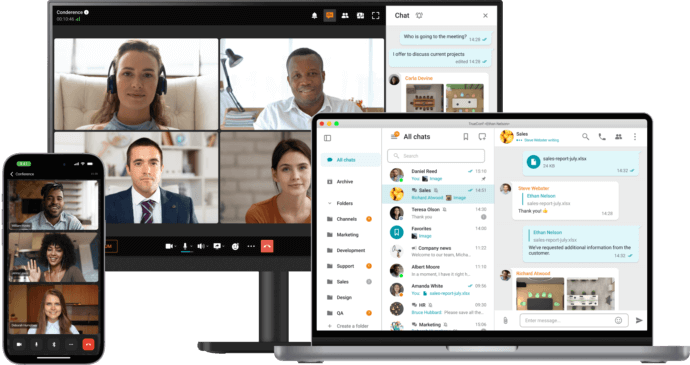
TrueConf is a secure collaboration and video conferencing solution tailored for enterprises that need full control over their communications. Unlike many mainstream platforms that operate exclusively in the cloud, TrueConf offers flexible deployment models, including fully on-premises installations. This approach allows organizations to keep sensitive data inside their private infrastructure, which is especially valuable for industries such as government, healthcare, finance, and education. The platform combines high-quality video meetings, team messaging, screen sharing, and webinar capabilities, making it a comprehensive alternative to global UCaaS tools while remaining cost-effective and scalable.
Pros
- Flexible deployment options: on-premises, cloud, or hybrid
- Full control over data storage and infrastructure
- High-quality video and audio conferencing
- Seamless integration with corporate IT systems (LDAP/AD, SIP/H.323, calendars)
- Scalable for large enterprises and government use cases
- Competitive pricing compared to global UCaaS platforms
Cons
- Requires IT resources for on-premises deployment and maintenance
- Lower brand recognition in some international markets
Security Features
- End-to-end encryption for video calls and data streams
- On-premises deployment keeps all data inside private infrastructure
- Multi-factor authentication and secure access controls
- GDPR and HIPAA compliance support
- Granular administrative policies for user management and data protection
Take your team communication to the next level with TrueConf!
A powerful self-hosted video conferencing solution for up to 1,000 users, available on desktop, mobile, and room systems.
2. Asana
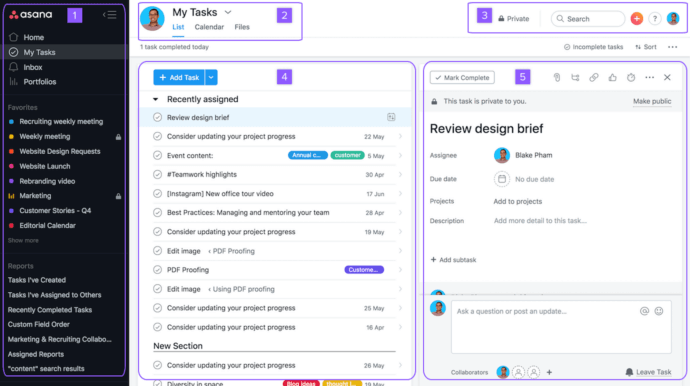
Asana emerges today as among the best-known project management and coordination platforms, designed to assist groups in organizing assignments, simplifying collaboration, and sustaining transparency throughout every initiative. Its adaptability appears across various formats — from detailed task tables and kanban-oriented boards to collaborative calendars and graphical timelines — empowering teams to oversee objectives, allocate responsibilities, and preserve momentum effectively. Through extensive connections with office essentials such as Slack, Google Workspace, and Microsoft Teams, Asana functions as a unified center that consolidates applications and workflows, removing disorder caused by fragmented solutions. For businesses of any scale, it provides both adaptability and focus, minimizing repetitive email exchanges and reinforcing responsibility throughout all phases.
Pros
- User-friendly interface offering diverse project formats (lists, boards, calendars, timelines)
- Extensive integrations across major office ecosystems
- Robust task oversight plus workflow automation resources
- Seamless integration with corporate IT systems (LDAP/AD, SIP/H.323, calendars)
- Expands smoothly for startups alongside international organizations
- Enhances responsibility while limiting communication overload
Cons
- Cloud-hosted exclusively; lacking on-premises deployment option
- Difficulty may escalate within particularly complex or larger projects without configuration
- Numerous advanced abilities restricted to premium or enterprise tiers
Security Features
- Two-factor authentication (MFA) plus single sign-on (SSO) compatibility
- Role-specific authorizations featuring detailed access rules
- Alignment with GDPR, SOC 2 Type II, and ISO/IEC 27001
- Comprehensive administration dashboard including activity tracking and audit records
- Enterprise-grade information export along with reliable backup options
3. Trello
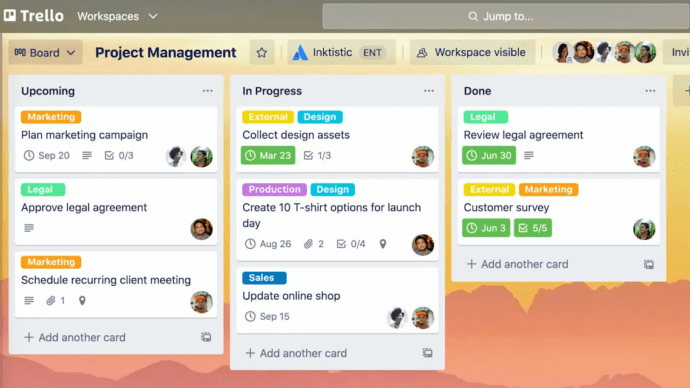
Trello remains recognized as a leading option for visual teamwork and project organization, giving groups an accessible and dynamic method to arrange assignments and processes using boards, lists, and cards. Its streamlined drag-and-drop layout converts project control into an efficient, seamless experience, enabling teams to maintain goals synchronized and progress transparent. In addition, Trello enhances its functionality via “Power-Ups,” introducing elements such as connected calendars, detailed analytics, time monitoring, and automation. This versatility has positioned Trello as a preferred solution for startups, creative departments, and small-to-medium organizations seeking a lightweight yet powerful style of project management.
Pros
- Simple, intuitive layout featuring drag-and-drop boards
- Extensive personalization using Power-Ups alongside automation
- Wide compatibility with Atlassian suite plus outside applications
- Perfect for visual task oversight and agile processes
- Cost-effective and practical for startups with smaller groups
Cons
- Restricted capacity within demanding, enterprise-level projects
- Cloud-exclusive setup; absent on-premises hosting alternative
- Enhanced options secured within premium plans
- May appear disorganized when excessive boards or Power-Ups exist
Security Features
- Two-factor authentication (2FA) along with single sign-on (SSO)
- Role-based permissions and administrative controls
- Adherence to GDPR and SOC 2 Type II requirements
- Secured information both during transfer and at rest
- Enterprise-grade management solutions offered through Atlassian Access
4. Microsoft Teams
Microsoft Teams functions today as a central hub of workplace collaboration and communication, merging chat, video sessions, document exchange, and app integrations within the trusted Microsoft 365 environment. Known as among the most extensively utilized platforms worldwide, Teams empowers companies to optimize workflows by merging interaction and teamwork into one unified space, lowering reliance on fragmented applications. Its strong alignment with Microsoft Office tools — Word, Excel, SharePoint, and Outlook — provides enterprises already committed to Microsoft an instant benefit. Designed for expansion, Teams adjusts smoothly to the requirements of corporations, universities, and government bodies, offering a consolidated solution for remote as well as hybrid operations.
Pros
- Tight integration inside Microsoft 365 suite (Word, Excel, SharePoint, Outlook)
- Combines messaging, video conferencing, document collaboration, and task coordination in one service
- Expands dependably for corporations, schools, and government entities
- Vast ecosystem featuring third-party extensions via the Teams App Store
- Broad international adoption with strong ecosystem backing
Cons
- Cloud-oriented approach with reduced adaptability for on-premises hosting
- May appear complicated or overwhelming for inexperienced members
- Performance could decline during enterprise-wide usage or intensive integrations
- Advanced compliance together with security elements frequently linked to premium packages
Security Features
- Encrypted communication during transfer and while stored
- Two-factor authentication (MFA) plus single sign-on (SSO) compatibility
- Alignment with GDPR, HIPAA, ISO/IEC 27001, and equivalent standards
- Enhanced threat defense powered through Microsoft 365 security services
- Role-specific access governance supported by detailed audit records
5. Zoom
Zoom has secured its position among the globe’s most prominent video collaboration and communication platforms, praised due to its clarity, adaptability, and dependability. Delivering high-definition video with audio meetings, engaging webinars, team chat, and cloud-driven telephony, it provides a versatile option that adjusts for businesses of any scale. Thanks to its streamlined layout plus multi-device accessibility, Zoom rapidly became dominant as a preferred tool for remote employment, hybrid teamwork, digital learning, and online events. Its broad integration marketplace links Zoom effortlessly with essential productivity software, guaranteeing fluid operations and heightened efficiency.
Pros
- Modern, user-friendly layout crafted for rapid onboarding
- Superior video along with audio supported by steady dependability
- Covers meetings, webinars, messaging, and cloud calling functions
- Vast integration catalog through the Zoom App Marketplace
- Expands smoothly across businesses, academia, and events
Cons
- Cloud-centric approach; missing complete on-premises hosting alternative
- Historical safety plus privacy breaches might spark worries
- Premium features (e.g., large-scale webinars, telephony) demand extra licensing
- Heavy dependence upon stable internet connectivity for top performance
Security Features
- End-to-end protection provided for meetings or calls
- Role-specific access management with advanced session controls (waiting rooms, passwords)
- Two-factor verification (MFA) and single sign-on (SSO) options
- Compliance ensured with GDPR, SOC 2, HIPAA, and other global frameworks
- Ongoing updates mitigating vulnerabilities while enhancing data protection
6. Google Meet
Google Meet appears today as an efficient, cloud-based conferencing and collaboration service closely integrated within Google Workspace (previously G Suite). Crafted for ease alongside accessibility at its foundation, it enables participants to start or attend sessions directly from Gmail, Google Calendar, or any updated browser — without additional downloads necessary. Equipped with tools such as live transcription, breakout sessions, and screen sharing, Google Meet has evolved into a dependable option for enterprises, schools, and individuals seeking a stable and straightforward video platform. Its seamless connection with Google Docs, Sheets, and Slides ensures collaboration feels natural, particularly for teams already engaged in Google’s environment.
Pros
- Smooth integration across Google Workspace (Gmail, Calendar, Docs, Sheets, Slides)
- No downloads necessary; operates entirely inside browsers
- Minimalist, intuitive interface encouraging rapid adoption
- Automatic captions with accessibility enhancements included
- Global infrastructure maintained by Google guaranteeing stable delivery
Cons
- Cloud-exclusive format; lacking on-premises hosting alternative
- Feature selection less sophisticated compared with Zoom or Teams
- Strong reliance upon Google Workspace subscription levels
- Reduced fit for extremely large enterprises handling complex scenarios
Security Features
- Encrypted transfer covering sessions and information streams
- Two-factor authentication (MFA) with single sign-on (SSO) through Google Workspace
- Adherence to GDPR, HIPAA, and other worldwide frameworks
- Embedded anti-abuse defenses, featuring host moderation, meeting tools, and safety locks
- Enterprise-grade administrative utilities enabling access governance and detailed audit reporting
7. ClickUp
ClickUp establishes itself as an all-encompassing productivity and collaboration center, combining project oversight, task monitoring, objective setting, and communication utilities within one unified ecosystem. In contrast to services focused on only one element of work, ClickUp provides a broad range of adaptable perspectives — spanning simple lists, kanban boards, Gantt diagrams, calendars, and interactive dashboards — enabling teams to mold the platform around their distinct processes. This adaptability has gained traction among startups, creative firms, and major enterprises aiming to replace scattered productivity apps with one coherent framework. Featuring integrated chat, collaborative documents, and automation options, ClickUp minimizes disruption from switching between tools, enhancing coordination and performance across groups.
Pros
- Unified center: project oversight, documentation, chat, and objectives in one environment
- Highly adaptable with diverse perspective choices (lists, boards, Gantt, calendars)
- Powerful automation features simplifying recurring assignments
- Links smoothly with hundreds of widely used office solutions
- Expands effectively for both small units and enterprise-scale organizations
Cons
- Cloud-oriented exclusively; lacking on-premises deployment capabilities
- May appear daunting for individuals preferring simplicity
- Advanced functions frequently restricted to upper-tier packages
Security Features
- Two-factor authentication (2FA) along with single sign-on (SSO)
- Role-specific authorizations supported by granular access rules
- SOC 2 Type II alignment and GDPR readiness
- Enterprise-grade administrative utilities including detailed audit tracking
- Encryption applied to information both while stored and during transfer
8. Flock
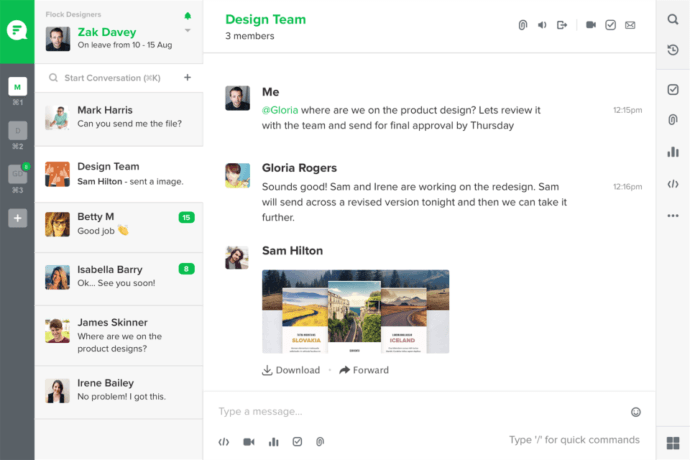
Flock identifies itself as a focused team collaboration and communication solution, designed to streamline discussions and enhance productivity for small through mid-sized companies. It unifies essential components — group messaging, video meetings, file transfers, task management, and searchable conversation history — all within a lightweight, user-friendly layout. Emphasizing speed alongside simplicity, Flock minimizes dependence on crowded email threads and instead delivers teams a centralized hub for everyday coordination. Featuring integrated productivity functions like shared lists, reminders, and polls, Flock moves past conventional messaging apps, positioning itself as a cost-conscious substitute for larger enterprise platforms.
Pros
- Simple, clear interface enabling fast onboarding
- Merges messaging, video calls, file transfers, and task management in one service
- Embedded productivity tools such as polls, reminders, and shared task lists
- More economical compared with bigger enterprise-class rivals
- Well-suited for startups plus small-to-medium businesses
Cons
- Fewer integrations compared with Teams, Slack, or ClickUp
- Cloud-exclusive service with no on-premises hosting alternative
- Might miss scalability plus advanced options for larger organizations
- Smaller ecosystem with reduced global brand awareness
Security Features
- Two-factor authentication (2FA) plus single sign-on (SSO)
- Protected data stored at rest and during transfer
- GDPR plus SOC 2 adherence ensuring data safety
- Role-oriented access rules and governance
- Administrative capabilities for overseeing accounts and users
9. Wire
Wire remains recognized as an exceptionally secure collaboration and communication system, designed with relentless emphasis on privacy and information protection. Originating from Switzerland, it merges messaging, audio and video conferencing, file exchange, and group collaboration into one comprehensive package. What differentiates Wire most is its consistent dedication to safety — each interaction is protected using end-to-end encryption automatically, guaranteeing confidential discussions stay insulated against intrusion. Its open-source base enables external verification and complete transparency of the security framework, fostering trust through accountability. Governments, enterprises, and institutions within tightly regulated fields increasingly adopt Wire whenever secrecy and compliance are mandatory.
Pros
- Automatic end-to-end encryption implemented across every communication
- Open-source structure supporting external audits and verifiable protection
- Flexible deployment including on-premises plus private cloud hosting
- Strong adherence with GDPR and enterprise-grade compliance benchmarks
- Well-suited toward governments, corporations, and high-regulation domains
Cons
- Smaller worldwide community plus limited brand recognition compared with dominant rivals
- Fewer outside integrations relative to platforms such as Teams or Slack
- Interface may appear less refined or intuitive for casual participants
- Enterprise implementations could involve greater expenses
Security Features
- Automatic end-to-end protection securing messages, calls, and files
- On-premises together with private cloud hosting ensuring full sovereignty
- Secure guest environments offered for external collaboration
- GDPR alignment supported using enterprise-grade certifications
- Smooth integration with identity plus access management (IAM) frameworks
10. Google Drive
Google Drive has transformed into a foundation of cloud-powered storage and collaboration, providing users and companies the capacity to safely save, retrieve, and distribute files through almost any device. Serving as an essential element of Google Workspace, it connects seamlessly with Docs, Sheets, Slides, and Gmail, supporting live co-editing and delivering a unified hub for digital resources. Thanks to its scalability, user-friendly layout, and flexible storage plans, Google Drive stands among the most broadly adopted collaboration systems worldwide, advancing productivity within enterprises, schools, and personal contexts.
Pros
- Smooth integration inside Google Workspace (Docs, Sheets, Slides, Gmail)
- Live collaboration with editing across shared content
- Simple file distribution plus strong permission settings
- Expandable storage options suited for both corporations and individuals
Cons
- Cloud-exclusive platform; lacking support for on-premises information hosting
- Restricted offline capability versus desktop-native utilities
- Needs reliable internet availability for effective performance
- Less precise enterprise management than specialized ECM solutions
Security Features
- Encryption enforced both while stored and throughout data transmission
- Two-factor authentication (MFA) alongside single sign-on (SSO) within Google Workspace
- Alignment with GDPR, HIPAA, SOC 2, and additional global frameworks
- Granular permission handling and context-based access policies
- Data loss prevention (DLP) with detailed audit trails for enterprise-level usage.
The Benefits of Using Secure Collaboration Tools for Your Business
Imagine a company where every department, from sales to legal, communicates freely without the shadow of data leaks. Secure platforms make that possible by combining powerful protections with intuitive collaboration features.
- Protect confidential data – A boutique law firm shares sensitive contracts with clients through encrypted channels, ensuring no unauthorized eyes ever see them.
- Ensure regulatory compliance – A hospital uses a GDPR- and HIPAA-compliant system, giving doctors peace of mind that patient records are safe and regulators satisfied.
- Build stronger client trust – A financial consultancy wins repeat business by showing clients that privacy-first platforms are part of their core values.
- Enable efficient remote work – A design agency with teams across three continents collaborates on projects seamlessly, running secure video calls and exchanging files without disruption, supported by structured team collaboration for accounting that keeps workflows aligned and client data protected.
- Prevent damaging incidents – A retail company avoids a costly breach when insider attempts to leak product data are blocked by strict access controls.
- Boost productivity securely – An engineering team focuses on innovation instead of security fears, knowing every chat, file, and task remains protected from intrusion.
How to Choose Secure Collaboration Tools
1. Identify Fundamental Business Priorities
A healthcare organization might emphasize video appointments and record exchange, while a creative agency depends on project oversight and file sharing. Clarify the team’s priorities — whether that means video meetings, workflow coordination, messaging, document control or document management — while accounting for company scale, sector demands, and the degree of information sensitivity.
The Department of Health of Ho Chi Minh City|Case Study
TrueConf video collaboration solution connected more than 100 hospitals in Ho Chi Minh and allowed converting quarterly medical examination and treatment briefings between the Department of Health and hospitals into online mode. 660 employees of the City Oncology Hospital can now collaborate with one another without any barriers, increasing both speed and efficiency of communications.

2. Evaluate Critical Security Measures
Move beyond surface terminology. End-to-end encryption, two-factor authentication, role-based controls, and adherence to GDPR, HIPAA, or ISO remain essentials. Ensure the provider reveals precisely where information resides and by what methods it is protected.
3. Consider Hosting Strategies
Does the environment require adaptability, tight control, or rapid growth? Enterprises in regulated fields may insist on complete on-premises deployment for sovereignty, while agile startups could adopt the cost efficiency and speed of cloud platforms. Hybrid configurations frequently achieve equilibrium between both models.
4. Check Compliance Standards and Certifications
When managing financial data, medical patient records, or sensitive state documents, compliance cannot be optional — it becomes survival. Validate that the selected solution matches relevant frameworks and delivers the certifications to demonstrate compliance.
5. Test Usability and Integrations
A system that frustrates employees will be one quickly abandoned. Conduct pilot trials to gauge ease of adoption and confirm seamless linkage with core essentials like CRMs, scheduling tools, and content libraries. A smooth user experience guarantees retention.
6. Assess Vendor Credibility and Support
Investigate the vendor’s track record: how did they handle breaches, address vulnerabilities, or communicate during emergencies? A reliable partner provides transparent reporting, proactive oversight, and responsive technical assistance when needed most.
Conclusion
The tools any business selects are not merely for supporting teamwork — they are equally for safeguarding sensitive information, ensuring compliance, and establishing trust with partners and clients. With cyber risks increasing and regulations growing tougher, depending on outdated or unsecured platforms is simply no longer viable.
By implementing secure collaboration platforms, organizations establish an environment where teams may innovate, collaborate, and expand without concern over data breaches or compliance gaps. From end-to-end encryption through multi-factor authentication and regulatory alignment, these solutions merge productivity with robust protection.
Related posts:
The Power of Online Collaboration: Unleashing Productivity with Best Tools
Unveiling the Power of Collaborative Apps for Productive Teams
What is Business Collaboration?
About the Author
Olga Afonina is a technology writer and industry expert specializing in video conferencing solutions and collaboration software. At TrueConf, she focuses on exploring the latest trends in collaboration technologies and providing businesses with practical insights into effective workplace communication. Drawing on her background in content development and industry research, Olga writes articles and reviews that help readers better understand the benefits of enterprise-grade communication.


Follow us on social networks