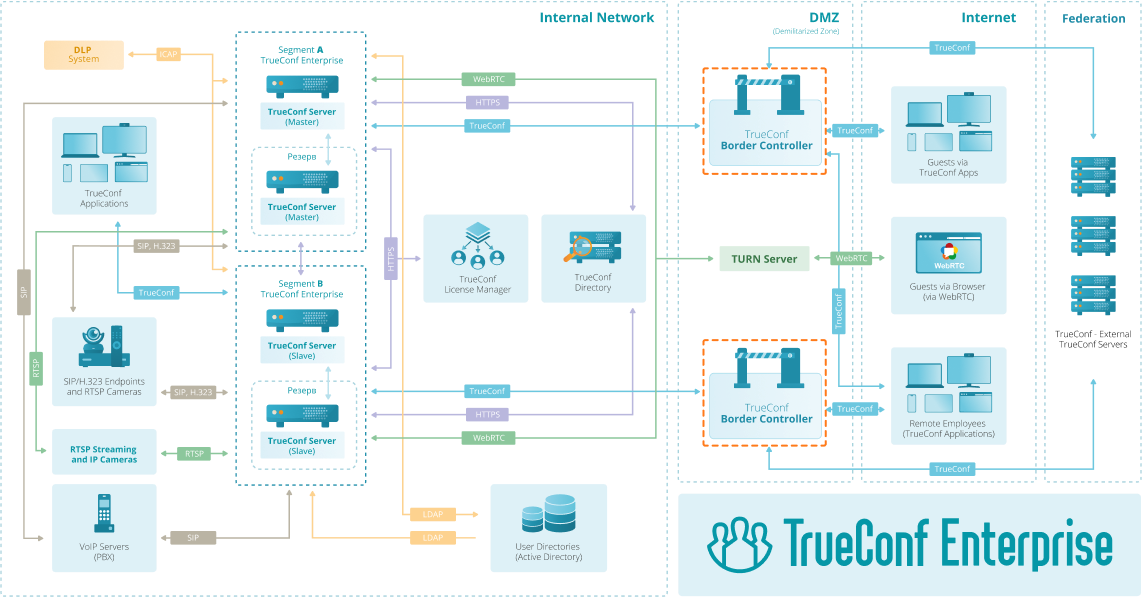
Border Controller
Mask the real IP address of your video conferencing system and restrict access to it from unwanted connections outside the corporate network.

Mask the real IP address of your video conferencing system and restrict access to it from unwanted connections outside the corporate network.
The edge controller ensures safe operation inside a closed corporate network, restricting access from unwanted connections to your video conferencing server if necessary.
Thanks to the border controller, data transfer is carried out only via the proprietary TrueConf protocol, ensuring the security of the connection.
The edge controller provides an additional degree of protection by hiding the real IP address of your video conference server.