The Most Secure Messaging Apps for Android — Comprehensive Overview
In today’s hyperconnected world, digital threats are escalating—from massive data breaches to state-backed surveillance and AI-enabled intrusion—making secure communication far more critical than ever.
Cybersecurity experts have sounded alarms about escalating privacy risks. For instance, AI assistants like Google’s Gemini are now granted default access to messaging content, sparking warnings about unchecked data exposure.
By mid‑2026, only 23% of U.S. smartphone users felt they had control over their personal data, while 40% were concerned about how companies use their information and 25% about government tracking.
These statistics illustrate an urgent need for tools that preserve privacy and protect users against surveillance and exploitation.
Purpose of this article: to synthesize the top secure messaging solutions from leading sources—into one comprehensive and coherent guide. Let’s explore how to communicate safely in the digital age.
Consumer-Grade Secure Messaging Apps
WhatsApp remains among the planet’s most commonly adopted communication platforms, relied upon by millions of individuals for routine interactions, corporate exchanges, and collective teamwork. Its broad popularity results not merely from practicality and cross-device compatibility but also from its consistent emphasis on confidentiality and digital protection. At the foundation of its defense architecture lies the Signal Protocol, a highly esteemed cryptographic system employed by prominent secure messaging solutions. Through this method, every transmission including written messages, audio conversations, video conferences, pictures, and recordings is secured with end-to-end encryption. This guarantees that nobody beyond the intended participants, not even WhatsApp or its controlling corporation Meta, is able to reach the content.
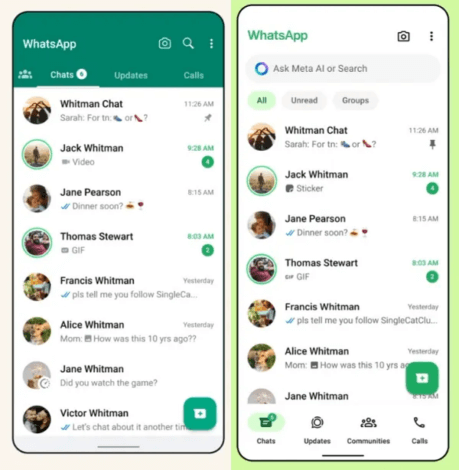
Beyond this essential encryption layer, WhatsApp introduces numerous privacy-improving capabilities that allow individuals improved authority over the ways their information becomes handled or preserved. For businesses, especially in online retail, integrating a WhatsApp AI chatbot for ecommerce can extend the platform’s secure communication framework to customer interactions – enabling encrypted, automated responses while maintaining data integrity. From self-erasing conversations and application locks to encrypted storage options and sophisticated chat restrictions, the service integrates protections that diminish dangers like illicit device entry, prolonged data retention, and exploitation of sensitive material. These elements position WhatsApp as a resilient solution for people who appreciate both ease and protection in their everyday exchanges.
Key Security Features
- End-to-End Encryption. Every private message, call, picture, and multimedia file is safeguarded with the Signal Protocol, blocking interception or unlawful entry by outside entities.
- Disappearing Messages. Conversations may be adjusted to erase automatically after a defined interval, reducing the likelihood of delicate information being archived or revealed later.
- Biometric and PIN Protection. Participants can secure particular conversations or the whole application with fingerprint authentication, Face ID recognition, or a PIN sequence, delivering an extra barrier of device-based protection.
- Advanced Chat Privacy. An updated configuration prevents outsiders from exporting dialogues, auto-retrieving media, or repurposing message material for AI models or external software tools.
- Encrypted Backups (Optional). WhatsApp grants the option to secure stored backups with a confidential password or a 64-character encryption key. This action restricts hosting providers from reading archived data, though the capability is not switched on by default.
Signal
Signal is broadly recognized as the platinum benchmark for private communication, delivering privacy-centered architecture and resilient end-to-end protection enabled automatically. Created by the nonprofit Signal Foundation, it equips individuals to interact beyond monitoring or personal exploitation.
Although maintaining simplicity, the platform integrates advanced defenses such as “sealed sender” which minimizes metadata disclosure, selectable usernames that enhance anonymity, and distinctive options including screenshot blocking on computers to resist invasive technologies.
Key Security Features
- Default End-to-End Encryption. Each text and conversation becomes instantly secured using the open-source Signal Protocol, with no additional adjustments required.
- State-of-the-Art Protocol. Employs the Signal Protocol, merging Double Ratchet, preliminary keys, and X3DH with Curve25519, AES-256, HMAC-SHA256 to ensure secrecy, forward and backward confidentiality, consistency, identity validation, and more.
- Metadata Reduction. Minimal session information is maintained (only previous connection date). Sealed sender conceals the details of originators from the central server.
- Open-Source and Auditable. Complete client along with server implementations (excluding anti-spam functions) are openly shared under the AGPL license, encouraging transparency and independent assessment.
- Device Linking Safeguards. Additional devices must undergo authentication (such as FaceID or passcode) with randomized reconfirmation prompts, efficiently blocking QR-code attacks aimed at activists.
- Desktop Screenshot Protection. Within Windows 11, Signal’s desktop platform applies DRM-style “screen security” that disables invasive mechanisms like Microsoft Recall, defending against unauthorized capture of conversations.
Telegram (Secret mode)
Telegram remains an extremely recognized, cloud-driven messaging service admired for its efficiency, adaptability, and extensive community-oriented features. It enables private one-on-one conversations, collective exchanges, multimedia transfers, and expansive public groups, frequently commended for its elegant design and smooth multi-platform experience.
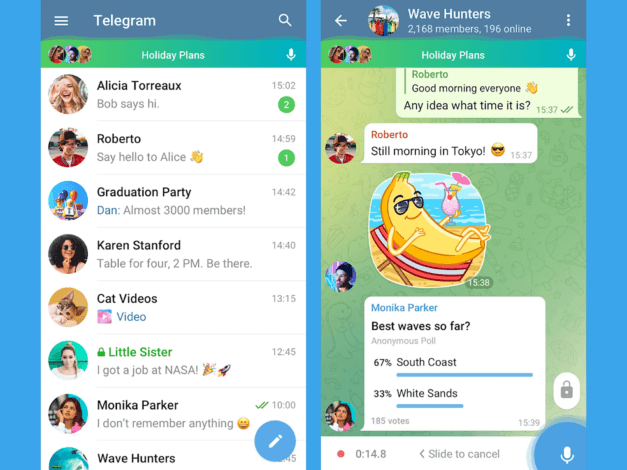
Nevertheless, its method regarding cryptography is layered and occasionally confusing: although Telegram applies protection across clients with their servers (client-server encryption), genuine end-to-end encryption (E2EE) becomes accessible exclusively via manually initiated “Secret Chats.” Standard conversations, particularly group dialogues, are not protected with end-to-end encryption, permitting Telegram itself the ability to review stored material.
Key Security Features
- Client-Server Encryption by Default. Every ordinary chat is secured between each client and Telegram’s servers, shielding transmissions during transfer yet still granting Telegram visibility into message substance.
- End-to-End Encryption (E2EE) in Secret Chats. Authentic end-to-end encryption functions solely when participants deliberately activate “Secret Chats.” Within this configuration, only the originator and recipient gain access to the content, excluding Telegram from decryption.
- MTProto 2.0 Protocol. Telegram depends upon its uniquely created MTProto 2.0 cryptographic framework for Secret Chats, structured to deliver authenticated security, forward secrecy, and message integrity. This system has received rigorous evaluation in scholarly analyses.
- Forward Secrecy. Secret Chats integrate forward secrecy, indicating that if any encryption credential becomes compromised, it cannot subsequently unlock previous communications.
Threema
Threema represents a Switzerland-based private communication platform developed around a firm Privacy by Design principle. In contrast with various dominant services, it prioritizes user anonymity, reduced metadata retention, and adherence to European protection regulations such as GDPR. Individuals are never obliged to disclose identifying elements like mobile numbers or email accounts; instead, every profile is assigned a randomly generated Threema ID, positioning it among the limited number of tools that permit completely anonymous usage.
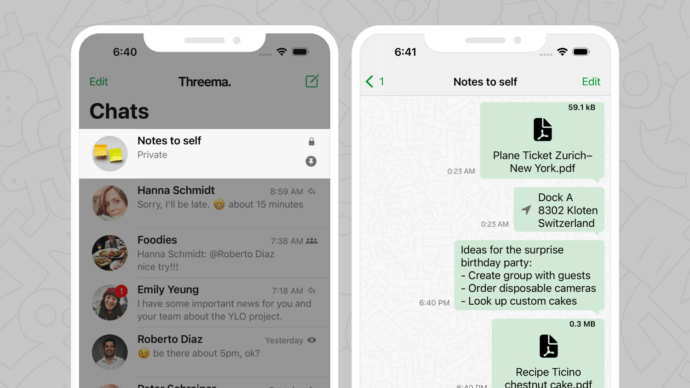
This platform functions absent commercial advertising and refrains from profiting through personal data. Rather, Threema implements an open financial structure, depending on single-purchase licenses for individuals and recurring subscription programs for companies. This structure guarantees that the organization’s sustainability aligns with customer trust and digital safety rather than surveillance-oriented business strategies.
Key Security Features
- Anonymity-First Registration. Participants are distinguished entirely by an automatically created Threema ID. Connecting a phone account or email remains optional, maintaining anonymity.
- Minimal Metadata. Data remnants are restricted to the lowest feasible level and erased whenever technically achievable. Threema prevents the generation of extended activity logs or invasive monitoring.
- End-to-End Encryption by Default. Every interaction type—chat messages, audio conversations, video calls, group exchanges, media transfers, and even status updates—remains strongly protected via the NaCl cryptographic library with ECC 256-bit keys and the XSalsa20 algorithm. Protection is permanently enabled and cannot be disabled.
- Secure Backup System (Threema Safe). Stored data copies are encrypted through scrypt-based key derivation, rendering them highly resistant against brute-force compromises while upholding anonymity.
- No Ads or Data Monetization. Threema never depends on targeted marketing or commercializing personal content. Its funding strategy revolves around one-time purchases and enterprise subscriptions, assuring that privacy protection is never undermined for financial gain.
Wire
Wire functions as a fully end-to-end protected collaboration system developed by Wire Swiss GmbH, an organization established by earlier Skype developers. Intended for both personal customers and major enterprises, Wire enables confidential interaction via messaging, audio, video meetings, and document transfers. The solution is designed with a strong priority on security, regulatory compliance, and adaptable deployment, making it highly appealing for institutions with rigorous data protection demands.
In contrast with various alternatives, Wire delivers automatic end-to-end encryption across all capabilities, guaranteeing that private material is viewable solely by intended recipients. With availability for numerous deployment styles, sophisticated cryptographic mechanisms, and adherence to international compliance standards, Wire is relied upon by governments, corporations, and privacy-driven organizations across the globe.
Key Security Features
- Default End-to-End Encryption. Every exchange, whether text messages, file transfers, audio calls, video meetings, or guest spaces, is safeguarded by default, ensuring that no unapproved entity (including Wire itself) can retrieve data.
- Flexible Deployment Options. Wire accommodates cloud-hosted, local on-premises, or blended environments, enabling institutions to match deployment with internal governance and infrastructure needs.
- Advanced Encryption Protocols:
- Proteus Protocol (derived from Signal Protocol) secures chats.
- DTLS and SRTP protect audio transmissions.
- Specialized secure transport protocols are applied to video conferencing.
- Cross-Device Synchronization. Participants may reliably connect as many as 8 devices, with encrypted session synchronization across all endpoints. Wire also incorporates protected guest spaces, allowing external collaborators to join without reducing confidentiality.
Silence
Silence represents a cost-free, community-driven Android program created to deliver end-to-end security for conventional SMS and MMS exchanges. Distinct from many comparable platforms, Silence eliminates the necessity for internet connectivity or centralized servers, positioning it as a privacy-oriented choice for people seeking confidential communication without dependence on external systems. It installs and operates like a normal SMS client, presenting a familiar layout while incorporating enhanced encryption mechanisms beneath the surface.
Through integration of the Signal Protocol, Silence guarantees that written transmissions between participants using the app remain completely protected, even without online access. It additionally secures local data storage via encryption, preserving confidentiality if the device becomes misplaced or stolen. Although notable for straightforward usage and offline reliability, further development of Silence has slowed considerably, leaving the application appearing inactive and generating concerns about unresolved vulnerabilities.
Key Security Features
- End-to-End Encryption for SMS/MMS. Communications exchanged between Silence participants are shielded with the Signal Protocol, ensuring protection without reliance on servers or internet access.
- Local Message Encryption. Entire conversation histories are safeguarded directly on the device, defending stored data from unauthorized entry if the handset is lost or stolen.
- Identity Verification. Contacts’ identities may be confirmed using fingerprint key comparison or QR code scanning, lowering susceptibility to man-in-the-middle intrusions.
- Drop-in SMS Replacement. Operates smoothly as the primary SMS application with no registration steps, account setup, or personal data collection. Contacts not using Silence can still send regular SMS messages, though without added protection.
- No Accounts or Signups. Phone number registration beyond SMS functionality is unnecessary, maintaining user anonymity and preventing centralized tracking.
Session
Session functions as an open-source, decentralized secure messenger engineered for privacy and metadata-free exchanges. Directed by the principle “Send conversations, not traces,” it removes identifiable markers and directs traffic across a resilient onion-based network, guaranteeing that no single server can ever determine both the sender alongside the recipient.
Key Security Features
- Anonymous Account Creation. No mobile number or email address must be provided. Users instead obtain a randomly produced 66-character alphanumeric Session ID serving as their identity.
- True Decentralization & Metadata Minimization. All transmissions travel through an onion-style system of community-maintained Service Nodes, preventing any node from identifying both origin and destination, substantially lowering metadata exposure.
- End-to-End Encryption by Default. Every exchange—including texts, media files, audio notes, and group discussions—is secured locally with the Libsodium library, ensuring that only authorized recipients can read content.
- Fully Open-Source and Independently Audited. The complete codebase is openly available under BSD-3-Clause, MIT, and GPL-3.0 licenses. Independent analysis by Quarkslab confirmed the security characteristics of the platform.
- Platform Coverage. Available across Android, iOS, Windows, macOS, and Linux desktops, with reliable cross-device synchronization included.
Dust
Dust functions as a privacy-centered platform developed around the concept of leaving zero lasting trace. Unlike mainstream communication tools that preserve interactions indefinitely, Dust guarantees that exchanges remain temporary, protected, and governed by the participant. The application targets individuals who emphasize discretion with security, providing assurance that their conversations cannot be retrieved, harvested, or abused by outside entities.
At its foundation, Dust integrates temporary messaging, end-to-end encryption, and comprehensive user controls to deliver a communication model where confidentiality dominates. Messages vanish immediately once viewed or automatically after 24 hours, while participants maintain the capability to retract or erase delivered material whenever desired. When combined with screenshot alerts and a firm no-data-collection approach, Dust delivers an uncommon degree of transparency alongside user empowerment in private communication.
Key Security Features
- Ephemeral Messaging by Default. Conversations are systematically removed from all devices immediately after being read, or within 24 hours if they remain unopened.
- Unsend Capability. Participants can withdraw messages whenever necessary, even after delivery, maintaining extensive authority over distributed information.
- Screenshot Detection. The application quickly notifies users if a recipient tries capturing a screenshot of the dialogue.
- End-to-End Encryption. Every transmission is safeguarded, guaranteeing that even Dust’s infrastructure cannot obtain message data.
- No Data Collection or Tracking. Dust highlights privacy through design, preventing information mining, third-party distribution, or indefinite storage.
Element (Matrix)
Element operates as a secure, decentralized communication and teamwork environment developed on the Matrix open protocol. Created by the original Matrix developers, it allows individuals, organizations, and governmental bodies to maintain digital independence by running their own servers or selecting reliable providers. Featuring strong end-to-end encryption, open-source verification, and extensive collaboration tools, Element has established itself as a primary alternative to centralized systems like Slack or Microsoft Teams.
Because it is rooted in Matrix, Element becomes naturally interoperable and resistant to obsolescence, ensuring that institutions are never confined to one vendor ecosystem. This mixture of safety, scalability, and openness has positioned Element as the trusted option for governments, defense institutions, public bodies, and enterprises requiring protected communication and strategic independence from proprietary infrastructures.
Key Security Features
- Decentralization & Self-Hosting. Organizations may fully self-host or rely on independent Matrix hosting, guaranteeing maximal authority over communication channels and resilience within critical operations.
- End-to-End Encryption by Default. All conversations (including large groups) are secured through Olm and Megolm protocols (Matrix’s adaptation of the Double Ratchet method), defending data even if infrastructure is breached.
- Secure Backups. Encryption credentials can be preserved safely, avoiding data loss across devices and sessions while keeping access limited to the account holder.
- Open-Source Transparency. Clients across web, desktop, and mobile (including Element X, reconstructed in Rust for performance and reliability) remain entirely open-source, enabling independent verification and building trust.
Enterprise & Compliance-Focused Platforms
TrueConf
TrueConf functions as a secure, enterprise-grade unified communications platform that consolidates on-premises messaging, UltraHD/4K video conferencing, and collaboration tools within a single solution. Designed specifically for high-security, closed-network environments, TrueConf ensures that organizations retain complete control over their communications and data. Unlike cloud-based alternatives, it can be deployed entirely within corporate infrastructure—supporting LAN, VPN, and fully isolated air-gapped installations—making it one of the most privacy-focused solutions available.
Its architecture and strict adherence to regulatory standards position TrueConf as the preferred option for governments, healthcare providers, financial institutions, and enterprises that require not only efficient collaboration but also uncompromising security and data sovereignty. Recognized by leading analysts such as Gartner, IDC, and Aragon Research, TrueConf stands out as a robust alternative to cloud-based services like Microsoft Teams, Slack, and Zoom in sensitive deployments.
Key Security Features
- Self-Hosted Architecture. Fully deployable on-premises, within a private LAN/VPN, or in isolated air-gapped environments, ensuring that all communications remain under organizational control.
- Comprehensive Encryption Suite:
- TLS 1.3 for signaling
- AES-256 for data protection
- SRTP and H.235 for media streams
- Proprietary protocols and codecs provide an additional defensive layer against interception.
- Compliance & Regulations. Supports ISO 27001, GDPR, and HIPAA requirements, enabling secure usage in highly regulated industries including healthcare, government, and finance.
- Secure Infrastructure Controls:
- IP-based access restrictions
- Border controllers to mask real server IP addresses
- Strong administrative access management to protect against insider and external threats.
Take your team communication to the next level with TrueConf!
A powerful self-hosted video conferencing and team messaging solution for up to 1,000 users, available on desktop, mobile, and room systems.
Rocket.Chat
Rocket.Chat remains an adaptable, enterprise-focused collaboration framework engineered around confidentiality, governance, and resilience. Crafted to support institutions across tightly regulated industries, it enables businesses and governmental agencies to safeguard complete authority regarding digital information and internal communication. Respected by military divisions, metropolitan administrations, and advanced security firms, Rocket.Chat thrives within mission-focused environments where integrity, compliance, and reliability are essential.
Its transparent open-source architecture under the MIT license, together with a dynamic GitHub network of roughly 30,000 engaged contributors, guarantees that this platform stays consistently evaluated, enhanced, and reinforced. Such openness delivers exceptional credibility when compared against proprietary alternatives, establishing Rocket.Chat as the preferred platform for entities requiring autonomy and sustainable longevity.
Key Security Features
- Open-Source Verification. Entirely open-source with a worldwide developer base constantly reviewing, optimizing, and confirming platform resilience.
- Deployment Versatility. Provides cloud-based, localized, hybrid, or completely isolated air-gapped implementations, allowing institutions to preserve sovereignty over sensitive operations.
- Zero-Trust Principles. Implemented via SSO, LDAP, OAuth, RBAC, auditing mechanisms, and highly detailed permissions (spanning more than 180–190 configurable policies).
- Compliance & Oversight. Conforms or integrates with GDPR, HIPAA, CCPA, ISO 27001, SOC 2, DoD IL6, and Iron Bank certifications, validated through independent audits.
- End-to-End Encryption (E2EE). Supported for personal exchanges and private channels, complemented with secure file-sharing encryption and restricted export functions.
Comparative Table
|
Name |
Platforms |
Encryption Type |
Metadata/Anonymity |
Open-Source/Audits |
Deployment Options |
Target Use-Case |
|---|---|---|---|---|---|---|
|
|
iOS, Android, Web, Desktop |
End-to-End (Signal Protocol) |
Collects metadata (contacts, IP, timestamps) |
Closed source, partial audits |
Cloud (Meta) |
Mass-market messaging |
|
Signal |
iOS, Android, Desktop |
End-to-End (Signal Protocol) |
Minimal metadata, stores only registration date |
Open source, audited |
Cloud (Signal Foundation) |
Secure personal communication |
|
Telegram |
iOS, Android, Web, Desktop |
MTProto (E2EE only in Secret Chats) |
Metadata collected, cloud chats not E2EE |
Partially open-source (clients), server closed |
Cloud (Telegram) |
Mass-market, flexible messaging |
|
Threema |
iOS, Android, Web, Desktop |
End-to-End (NaCl) |
No phone number required, minimal metadata |
Closed server, open-source clients |
Cloud (Switzerland-based) |
Cloud (Switzerland-based) |
|
Wire |
iOS, Android, Desktop, Web |
End-to-End (Proteus / MLS) |
Some telemetry, phone number not required |
Open-source, Swiss company |
Cloud (EU), On-Premises |
Enterprise, business messaging |
|
Silence |
Android |
End-to-End (Signal Protocol, SMS/MMS-based) |
No metadata stored, works over SMS |
Open-source |
Local (SMS), no server |
Secure SMS, offline use |
|
Session |
iOS, Android, Desktop |
End-to-End (Signal fork + onion routing) |
No phone numbers, decentralized routing via LokiNet |
Open-source |
Decentralized P2P |
Anonymity, privacy |
|
Dust |
iOS, Android |
End-to-End (custom implementation) |
Ephemeral chats, minimal metadata |
Closed source |
Cloud |
Ephemeral privacy messaging |
|
Element (Matrix) |
iOS, Android, Desktop, Web |
End-to-End (Olm/Megolm) |
Metadata depends on server, self-host possible |
Open-source, independent audits |
Cloud, Self-host (Matrix server) |
Team collaboration, federation |
|
TrueConf |
Windows, macOS, Linux, iOS, Android, Web |
Transport + On-Prem E2EE (TLS, SRTP, AES) |
Full control by organization |
Proprietary server, client apps verified |
On-Premises, Private Cloud |
Enterprise/Government |
|
Rocket.Chat |
iOS, Android, Desktop, Web |
Transport encryption + optional E2EE |
Metadata depends on deployment |
Open-source, frequently audited |
Cloud, Self-host, On-Premises |
Enterprise / Regulated use |
Conclusion
As cyber risks increase and anxieties around monitoring intensify, private messaging applications have emerged as critical instruments for defending individual confidentiality and shielding highly sensitive institutional exchanges. The ecosystem of private messengers is varied: user-friendly services like WhatsApp and Signal combine accessibility with robust encryption, while alternatives such as Threema, Wire, and Session emphasize pseudonymity, distributed architecture, and information minimization. Other options, including Dust, address narrower contexts, delivering temporary or offline-protected interactions.
For corporations and administrations, offerings like TrueConf, Rocket.Chat, and Element (Matrix) distinguish themselves by providing locally hosted or hybridized infrastructures, comprehensive regulatory conformity, and operational durability—capabilities extending far beyond what common consumer apps deliver.
Ultimately, the “most resilient” messaging service is context-driven. Regular users may select Signal or Threema for everyday confidentiality, campaigners and reporters may gravitate toward Session or Element for decentralization and anonymity, while strictly regulated sectors may demand enterprise-caliber frameworks such as TrueConf or Rocket.Chat to ensure compliance and sovereignty of data.
In times where digital interaction represents both essential connection and significant exposure, selecting an appropriate solution is no longer merely convenience—it becomes a deliberate choice concerning confidentiality, reliability, and organizational authority.
About the Author
Olga Afonina is a technology writer and industry expert specializing in video conferencing solutions and collaboration software. At TrueConf, she focuses on exploring the latest trends in collaboration technologies and providing businesses with practical insights into effective workplace communication. Drawing on her background in content development and industry research, Olga writes articles and reviews that help readers better understand the benefits of enterprise-grade communication.



Follow us on social networks