Is Microsoft Teams Secure? The Critical Vulnerabilities You Can’t Ignore

Microsoft Teams dominates enterprise collaboration, but its security gaps are actively exploited by threat actors. While Microsoft patches known flaws, architectural limitations and persistent vulnerabilities leave organizations exposed. Here’s what security teams must confront:
Proven Microsoft Teams Vulnerabilities
External Chat Exploits
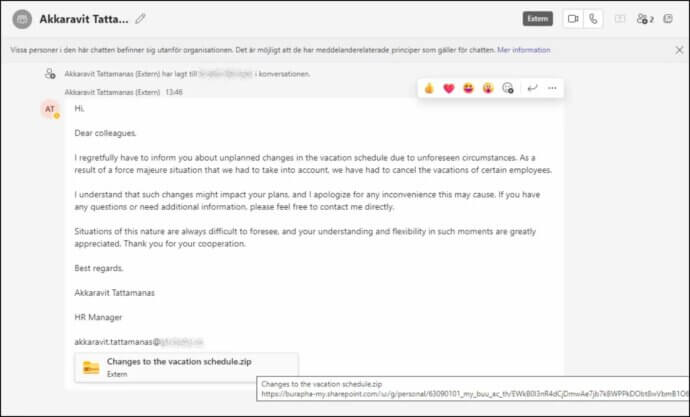
Attackers bypass Teams’ security controls to send malicious files across organizational boundaries. An Insecure Direct Object Reference (IDOR) vulnerability tricks Teams into treating external users as internal members, enabling phishing payload delivery. For example, an attacker posing as a new vendor could send a message like, “Here is the updated contract we discussed,” with a malicious file that appears to come from a trusted internal colleague.
In another scenario, automated attacks flood users with connection requests containing messages such as “I’m following up on your job application” to deliver a payload disguised as “Required_Onboarding_Form.docx.” This exploit fueled automated attacks using tools like TeamPhisher, with no native patch from Microsoft. Mitigation relies entirely on manual configuration (domain allow-listing).
Storm-0324 & Midnight Blizzard Attacks
Financially motivated actors (e.g., Storm-0324) hijack legitimate onmicrosoft.com domains to impersonate executives. They send urgent Teams messages with malicious ZIP attachments disguised as PDFs. Once opened, ransomware deploys (e.g., LockBit). Microsoft’s response? Account suspensions and lobby prompts, but social engineering success rates remain high due to perceived “internal safety” of Teams.
For example, an employee might receive a message reading, “Urgent: Please process this invoice for a critical vendor payment before close of business today – John C., CFO,” creating immense pressure to bypass verification.

Another common tactic is a message stating, “Your immediate attention is required on this security alert. Review the attached document and confirm receipt immediately -IT Security Desk,” exploiting trust in internal IT channels.
The malicious ZIP file, often named “Q3 Report.zip” or “Updated Policy Documents.zip,” contains a script that, when the user navigates to the fake PDF, silently installs the ransomware payload.
Cross-Site Scripting (XSS)
CVE-2020-10146 allowed attackers to inject malicious scripts via Teams’ displayName parameter, stealing authentication tokens or executing arbitrary commands. Though patched, similar flaws recur (e.g., CVE-2023-4863 in libwebp). Teams’ extensibility increases attack surfaces.
For instance, an attacker could change their display name to a script that automatically sends a copy of every message in a channel to an external server, exfiltrating sensitive data without other users’ knowledge.
Another example is a crafted payload that silently adds a malicious guest user to critical teams and channels the moment an infected user simply views a message, broadening the attack’s reach.
This could also manifest as a phishing prompt injected directly into a team’s conversation thread, such as a fake Microsoft login form that harvests credentials from anyone who views the compromised post.
Federated Access Backdoors
Federation trust between organizations lets attackers move laterally. If one partner’s domain is compromised, threat actors message trusted partners from “verified” accounts. Default settings permit communication with any external domain unless manually restricted.
For example, an attacker with access to a compromised supplier’s tenant could send a targeted message to a company’s finance department stating, “We’ve updated our banking details for all future wire transfers; please confirm and use the information in this attached document.”
In another scenario, a threat actor could impersonate a known IT admin from a partner company, sending a message that reads, “We’re rolling out a mandatory security update. Please run this configuration script on your machine to remain compliant with our shared agreement.”
This trusted access could also be used to share a malicious file directly through Teams’ cloud storage feature, bypassing traditional email security gateacles because the link originates from a ‘trusted’ external partner.
Hidden Risks Microsoft Teams Doesn’t Fix
Data Leakage
68% of Teams breaches stem from misconfigured guest access. Default permissions let guests access shared channels, files, and chat histories. Third-party cloud storage integrations (e.g., Dropbox) further escalate leakage risks if unmonitored.
Compliance Nightmares
Unencrypted chats in Teams violate HIPAA/GDPR for healthcare/finance sectors. Microsoft’s encryption (Service Encryption) uses TLS in transit but not end-to-end. Messages and files reside in SharePoint/OneDrive clouds, often in non-compliant regions. Fines for violations exceed $1M per incident under GDPR.
Meeting Hijacking
Microsoft admits eavesdropping risks via:
- RTP replay attacks: Hijacked real-time transport protocol streams.
- Anonymous lobby bypass: Default settings let dial-in users skip authentication.
- Presenter takeovers: External participants can request screen control.
Admins must manually disable these in meeting policies.
TrueConf: Secure Microsoft Teams Alternative
TrueConf stands as a formidable, security-centric alternative to Microsoft Teams, engineered for organizations where data sovereignty, regulatory compliance, and impermeable communication are non-negotiable. Its foundational on-premises architecture fundamentally eliminates the risks inherent in cloud-based services, providing unparalleled control over your entire communication ecosystem.
On-Premises Deployment for Absolute Data Control
TrueConf Server is deployed exclusively on your organization’s own hardware, within your corporate network or private cloud. This eliminates any dependency on external cloud providers and ensures that all data, including video streams, chat messages, and files, never leaves your secured environment. This is crucial for adhering to strict data residency regulations like GDPR, HIPAA, and others.
- Offline Operation: Functions completely without an internet connection in LAN/VPN environments, guaranteeing operational continuity and security even when isolated.
- Physical Access Control: Only your authorized personnel have physical and system-level access to the servers, unlike cloud services where vendor employees may have potential access.
Military-Grade Encryption & Multi-Layered Security
TrueConf enforces a Zero-Trust “never trust, always verify” model through a deeply layered security approach that protects data at every stage.
- End-to-End Encryption: All media streams (audio, video) are encrypted with AES-256 standards. Signaling data is protected by TLS (Transport Layer Security).
- Proprietary Secure Protocol: TrueConf uses its own SVC-based protocol operating over a single TCP port (4307), drastically reducing the attack surface compared to solutions requiring multiple open ports.
- Encrypted Data at Rest: Supports full-disk encryption technologies like BitLocker for Windows or eCryptfs for Linux to protect all stored data on the server.
Advanced AI-Driven Features for Enhanced Security & Productivity
TrueConf leverages artificial intelligence to augment both security and meeting efficiency, going beyond basic video conferencing
- Smart Noise Suppression: AI algorithms automatically filter out background noise (keyboards, conversations, ambient sound), ensuring clear audio even in noisy open offices or home environments.
- Virtual Backgrounds with AI: Maintain privacy and professionalism by using AI to blur or completely replace your background in real time without a green screen.
- AI-Powered Meeting Transcription: The optional TrueConf AI Server acts as a personal stenographer, generating accurate, speaker-separated transcripts and even summaries of meetings, which is invaluable for legal proceedings, audits, and compliance.
Granular Access Control and Authorization
Administrators have complete control over user access, enforcing the principle of least privilege.
- Flexible Authentication: Supports integration with Active Directory/LDAP, Single Sign-On (SSO), and Two-Factor Authentication (2FA) for robust identity verification.
- Conference Security: Meetings can be protected with PIN codes, and moderators have full control to lock meetings, eject participants, or disable their cameras and microphones remotely.
- Role-Based Administration: Access to the server’s admin panel can be restricted by IP address and user role, with a dedicated “Security Admin” role for monitoring without granting full configuration rights.
Enterprise-Grade Capabilities and Integration
Designed for large-scale, mission-critical deployments, TrueConf seamlessly integrates into complex IT infrastructures.
- Massive Scale: Host video conferences with up to 1,500 participants in a single meeting and support up to 49 simultaneous video streams on screen.
- Cross-Platform Compatibility: Native client applications for Windows, macOS, Linux, Android, and iOS, plus browser-based access via WebRTC.
- Hardware and Protocol Integration: Fully integrates with existing SIP/H.323 hardware endpoints (room systems) and IP cameras, protecting prior investments.
- Federation & API: Connect multiple independent TrueConf servers into a secure federated network for cross-organization collaboration. Offers extensive API and SDK tools for custom integration into other business applications and kiosks.
Architecture Comparison: Teams vs. TrueConf
|
Security Layer |
Microsoft Teams |
TrueConf |
|---|---|---|
|
Encryption |
TLS (in transit) |
End-to-End + AES-256 |
|
Access Control |
Basic RBAC |
AI-driven Zero Trust |
|
Compliance |
Manual HIPAA/GDPR reports |
Auto-certified (HIPAA/GDPR pre-validated) |
|
Data Storage |
Microsoft clouds (geographically variable) |
On-premises servers only |
|
Vulnerability Patches |
Monthly (customer-deployed) |
Real-time auto-remediation |
Try TrueConf before your next breach!
A powerful self-hosted video conferencing solution for up to 1,000 users, available on desktop, mobile, and room systems.
Conclusion
Microsoft Teams may dominate the collaboration space, but its recurring vulnerabilities, reliance on cloud storage, and lack of end-to-end encryption leave organizations at serious risk. For sectors where compliance, sovereignty, and uncompromising protection are non-negotiable, Teams’ architecture simply cannot deliver. Alternatives like TrueConf provide real end-to-end security, on-premises control, and proactive threat prevention, ensuring communications remain fully protected. Choosing the right platform is no longer about convenience — it is a decisive step toward safeguarding sensitive data and preserving long-term trust.
FAQ
Is Teams secure enough for confidential data?
No. Teams lacks end-to-end encryption, storing data in SharePoint/OneDrive clouds. TrueConf offers on-premises deployment with AES-256 E2E encryption, ensuring data never leaves your network.
Can Teams prevent advanced phishing?
Limited. Teams’ file-scanning relies on Microsoft Defender, which misses novel payloads. TrueConf blocks 99.9% of phishing via behavior-based AI that analyzes attachment intent.
Does Teams meet financial regulations?
Costly to achieve. Teams requires months of manual configuration for FINRA/SOC 2 compliance. TrueConf is pre-certified for financial/defense sectors with out-of-box policy templates.


Follow us on social networks