Video Conferencing Encryption
Definition of Data Encryption
Encryption is a fundamental cybersecurity method in which information is converted from a readable format into encoded form so that only users with access to a secret key or password can decrypt it. In other words, data is transformed into an unusable form known as ciphertext. If intercepted, it appears scrambled to malicious actors. This prevents stolen content from being used, since attackers cannot read it as plaintext.
Encryption schemes are implemented using software called encryption algorithms or ciphers, which can only be broken with significant computing power. The two most common encryption methods are symmetric and asymmetric, referring to whether or not the same key is used for both encryption and decryption.
History of Cryptography
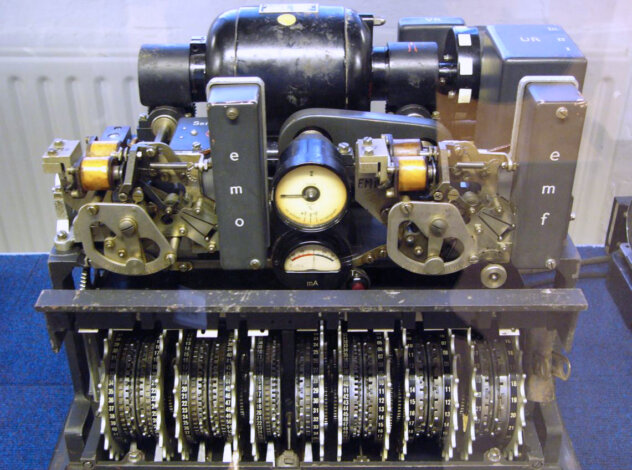
The history of cryptography spans about 4,000 years old, beginning with the simple substitution of letters with other letters or symbols. As societies evolved, encryption techniques became more sophisticated, incorporating mathematical formulas, mechanical devices, and rotor machines.
So, which video conferencing services provide the most reliable privacy protection? Which messaging apps lack end-to-end encryption and fail to meet security standards? With so many encrypted communication tools available, which features are truly essential?
Video conferencing encryption is necessary to ensure confidentiality during online meetings, seminars, and negotiations. Even if an intruder intercepts the video stream, they will not be able to decrypt it.
Common Use Cases for Encryption
Modern cryptography methods are used for secure data exchange between web servers and browsers, ATM transactions, computer networks, electronic document management, online storage, messaging, and video communications. Encryption is employed across both private and public sectors, as every organization must keep sensitive information private and secure.
Web Browsing
HTTPS (Hypertext Transfer Protocol Secure) is typically indicated by a closed padlock icon to the left of the URL in a browser’s address bar. This protocol ensures safe communication and data transfer between a user’s browser and a website via up-to-date and valid TLS (Transport Layer Security), or its predecessor SSL (Secure Sockets Layer).
HTTPS establishes a secure connection by using public or private keys to generate a shared symmetric key for encryption and authentication. However, unlike end-to-end encryption, HTTPS protects information only in transit. In other words, it does not provide full privacy protection, but it does keep sensitive data safe during online exchanges. For additional security, private browsing modes may be used.
Secure Messaging
End-to-end encryption (E2EE) is a secure communication method in which only the sender and intended recipient can view a message’s contents. It prevents personal information from being decrypted by Internet service providers (ISPs), application providers, hackers, or other unauthorized parties.
E2EE is an excellent choice for security-conscious users and organizations. While it does not guarantee complete protection, its security level is considered very high. Many popular messaging services and email providers, including Signal, WhatsApp, and Proton Mail, implement E2EE to protect data in transit.
Video Conferencing
As many organizations have adopted hybrid and remote working formats, video conferencing has become the primary and most effective way to connect distributed teams. Despite advanced encryption methods, risks still remain when protecting sensitive communications.
During video meetings, participants may discuss not only work-related matters but also confidential topics. The leakage of such information could damage both a company’s reputation and the personal lives of employees. Therefore, it is advisable to implement self-hosted video conferencing solutions that encrypt intra-corporate communications end-to-end, can operate within LAN/VPN environments, and comply with GDPR and HIPAA.
For additional security, a VPN can protect sensitive data shared during meetings. Tools like ExpressVPN for PC ensure that online activities remain encrypted, even outside corporate networks.
Why Do You Need Video Conferencing Encryption?
The purpose is to protect financial resources and safeguard a company’s reputation. With the widespread use of computer systems, information has become a core asset. This is why governments and private companies devote increasing attention to information security. Properly implemented cryptographic algorithms do not completely eliminate the risk of data compromise but significantly reduce it.
When communicating via corporate video conferencing systems, employees may unintentionally disclose sensitive information. For example, exposing an employee’s political or religious views or attitudes toward minorities can cause personal reputational harm and damage the company’s brand. Stolen information can also be exploited for fraud or blackmail.
The theft of trade secrets is common practice. Therefore, protecting company data is critical. Strong encryption makes unauthorized access and decryption difficult and expensive, and thus less attractive to competitors.
Implementation of Video Conferencing Encryption
Let us examine encryption implementation in modern VC applications using the example of TrueConf Server. This product does not require an Internet connection and can operate in a closed network.
The latest version of the OpenSSL TLS protocol, which encrypts data at the transport layer, is used to transmit signaling information. The protocol works as follows:
-
- The client sends a connection request to the server, providing a list of supported encryption software, algorithms and hash functions.
- The server selects the most secure algorithms from the list that it supports and informs the client of its choice.
- The server sends a digital certificate to the client for authentication.
- The client verifies the certificate’s validity using root certificates from trusted Certification Authorities before establishing the connection.
- A secure connection is established between the client and server. It is encrypted with a session key generated using the Diffie-Hellman key exchange.
WebRTC connections also support DTLS and SRTP protocols. For SIP and H.323 devices, SRTP and H.235 are supported, respectively.
- DTLS is a modified TLS protocol designed to protect datagram connections. It is often used over UDP, which is typically employed for media transmission. DTLS retains TLS security features while compensating for UDP’s shortcomings, such as lack of integrity guarantees and delivery confirmation.
- SRTP is used to encrypt voice traffic in VoIP. Its advantages include simplicity, efficiency, timestamping and packet numbering for media stream synchronization, and AES hardware support.
- H.235 is a specification that defines security features for the H.323 protocol in multimedia transmissions. For user authentication, H.235 supports passwords, digital certificates, and public key encryption.
Security and encryption for H-Series (Sourse)
TrueConf Server also uses a modified VP8 codec with SVC support for video encoding. This custom approach makes it more difficult to decrypt video streams using standard methods.
It is common practice to encrypt streams with symmetric-key algorithms. The AES algorithm, adopted as a standard by the US government, is one of the most widely used encryption methods.
The principle of AES is straightforward: a 128-bit input block is transformed into another block using a secret encryption key. The key length — 128, 192, or 256 bits — determines the security level.
The transformation is repeated several times (10, 12, or 14 rounds, depending on the key length). Each round uses a round key derived from the main secret key. TrueConf Server employs AES-256, the strongest variant, to secure media data.
The AES algorithm scheme (Source)
Modern Intel, AMD, and ARMv8 processors include the AES hardware support, which significantly enhances video communication security without performance loss. For additional protection of connections between corporate network segments, VPN gateways with end-to-end encryption can be used. In this case, security is provided by the IPsec protocol family.

Follow us on social networks