Security Policies for an Organization: Templates, Examples & Best Practices

Security policies are the backbone of a stable and resilient organization. They define clear principles for how information, systems, and resources should be managed and protected. Without consistent policies, employees may lose guidance, resulting in uneven practices and higher risks of data breaches, compliance violations, and operational disruptions.
Why Are Workplace Security Policies and Procedures Important?
- Protecting People and Assets
Security policies safeguard staff, clients, and visitors, maintaining a safe workplace environment. They also assist protecting physical property such as equipment, inventory, and sensitive information against theft, harm, or abuse.
- Maintaining Data Privacy and Compliance
Security procedures support ensure compliance with regulations and industry standards, while safeguarding personal and business data against breaches or unlawful access.
- Reducing Risks and Liabilities
Clearly defined protocols decrease the probability of accidents, cyberattacks, and workplace incidents. By adhering established procedures, companies lower their legal and financial obligations, while also showing due diligence to regulators and stakeholders.
- Enhancing Employee Awareness and Accountability
Policies set standards for conduct and outline the proper actions to follow in various situations. Training employees regarding these policies increases awareness, promotes accountability, and supports a culture of security throughout the workplace.
- Ensuring Business Continuity
Security incidents may interrupt operations, causing extended downtime and financial damages. Strong policies and procedures equip organizations to react rapidly, recover efficiently, and preserve business continuity during the face of emergencies.
Types of Security Policies in Every Organization
Program policy
A program framework outlines the essential strategy and overarching structure for an enterprise’s protection initiatives. It establishes the highest-level direction for the organization’s security posture and serves as the cornerstone upon which all other security policies are built. This type of policy is usually wide in coverage, describing the organization’s defense principles, long-term security objectives, and the duties of leadership and employees alike.
A program policy provides clarity on the organization’s overall philosophy toward risk management, compliance, and data protection. It explains why security is critical to business continuity and how it supports regulatory obligations, customer trust, and competitive advantage. By addressing topics such as governance, accountability, and the alignment of security with business strategy, the policy ensures that protection efforts are not isolated technical tasks but integral parts of the organization’s mission.
This guideline establishes the groundwork for every subsequent safety-oriented regulation, offering a consistent framework for issue-specific and system-specific policies. It also guarantees that managerial dedication remains clear and dependable, signaling to stakeholders, partners, and regulators that security is taken seriously at the highest level. Ultimately, a program policy defines the “big picture” vision for security and communicates that vision across the enterprise.

Issue-specific policy
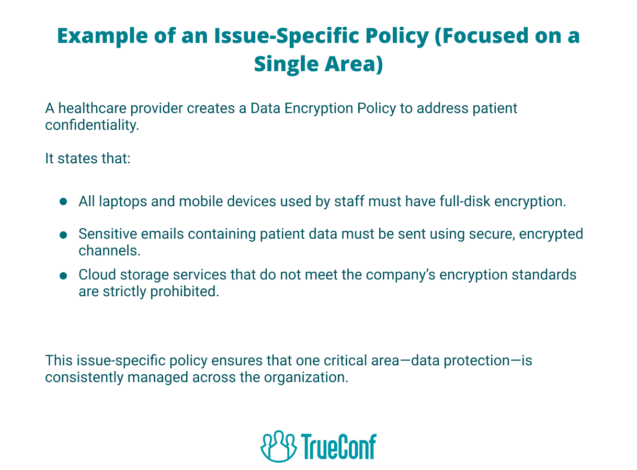
An issue-focused guideline manages distinct challenges or categories of exposure inside the enterprise, providing detailed rules for areas that require special attention. While a program policy defines the broad security philosophy of the organization, issue-specific policies narrow the focus to address particular risks, technologies, or processes that demand customized guidance.
For example, an organization might establish a rule devoted to messaging practices, online network permissions, or information protection. Additional issue-specific areas often include password management, acceptable use of mobile devices, handling of personal data, third-party vendor access, or CSPM cloud security practices. Each of these areas presents unique risks that cannot always be addressed adequately at the program level.
Such directives deliver greater clarity compared with program directives by spelling out the exact expectations, rules, and procedures for employees and contractors. They not only outline what behaviors are allowed or restricted but also provide step-by-step requirements for compliance. Issue-specific policies are especially important in industries with strict regulations, such as finance, healthcare, or government, where non-compliance could lead to significant penalties or reputational harm.
These policies instruct staff regarding ways to approach targeted scenarios in a secure and lawful fashion. They serve as a bridge between broad security goals and day-to-day operations, ensuring that employees understand both the “why” and the “how” of proper security practices. By doing so, issue-specific policies reduce ambiguity, minimize risk, and reinforce accountability across the enterprise.
System-specific policy
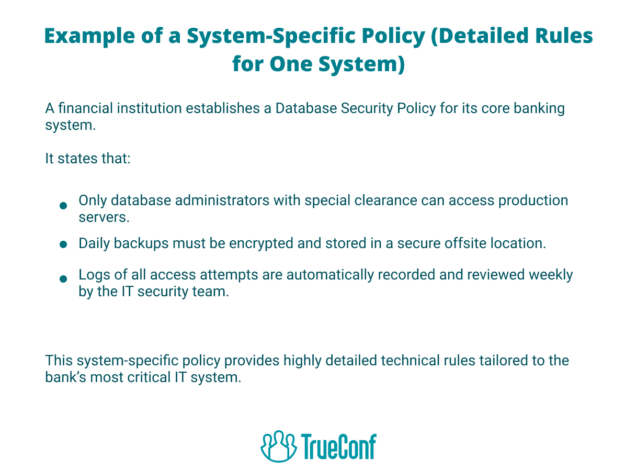
System-specific policies focus on individual platforms, infrastructures, or applications, providing detailed technical and operational requirements for their protection and management. They outline how unique assets such as databases, servers, and cloud environments should be configured, maintained, and monitored, covering aspects like authentication, backup procedures, patching, and logging.
These directives are highly precise, often including access controls, configuration benchmarks, and oversight methods tailored to each system. By enforcing consistent technical standards, system-specific policies minimize security gaps, ensure compliance, and strengthen the organization’s overall security posture.
Elements of an Effective Security Policy
1. Purpose and Scope. Each protection guideline must explicitly outline its objective (e.g., safeguarding information, blocking unlawful entry) and coverage — identifying whom it affects (staff, partners, suppliers) and which elements it includes (platforms, connections, physical resources).
2. Roles and Responsibilities. The policy should define who is responsible for what. For instance, leadership supplies funding and supervision, technical teams apply and supervise safeguards, while personnel observe the procedures. Strong responsibility reduces misunderstanding and supports maintaining adherence throughout the enterprise.
3. Acceptable Use of Resources. Staff members need awareness regarding which actions represent proper utilization of corporate resources, including devices, communication tools, and online connectivity. Through establishing clear limitations, enterprises diminish threats such as information breaches, harmful software intrusions, and exploitation of confidential data.
4. Access Control and Data Protection. An effective directive explains where entry gets provided, altered, and withdrawn, adhering to the principle of minimum privilege. It must further address information defense measures including encoding, reliable archiving, and proper elimination techniques, guaranteeing data stays protected.
5. Incident Response and Reporting. Protection events may arise regardless of the strongest precautions. Guidelines should deliver precise procedures for incident response on how to detect, notify, and react to violations or unusual actions. This approach guarantees rapid control, reduces harm, and supports preserving confidence among customers and collaborators.
6. Review and Enforcement. Effective policies are living documents. They require assessment consistently to remain synchronized with emerging dangers, innovations, and standards. Simultaneously, the directive needs to specify penalties for infractions, guaranteeing staff recognize that protection is regarded firmly.
Who is responsible for making an organization secure?
The simple reply becomes: everyone! Accidental human mistakes and mishaps trigger 90% of information exposures. Each worker, associate, vendor, client, or application participant remains vulnerable to psychological manipulation techniques (baiting, phishing, targeted phishing, voice scams, etc.) that attackers employ to deceive individuals into releasing confidential details. Criminals subsequently exploit those details to penetrate the enterprise’s platforms and records.
Questions to Ask When Building Your Security Policy
When designing or updating a protection directive, raising the proper inquiries guarantees it stays understandable, workable, and consistent with organizational priorities. Several important considerations include:
- What exactly are we attempting to secure? Identify essential resources including client records, proprietary knowledge, monetary platforms, or tangible machinery.
- Who requires entry, and for which elements? Clarify duties, accountabilities, and permission tiers to avoid needless disclosure of confidential details.
- Which dangers and vulnerabilities appear most significant for us? Examine both outside challenges (hacking, robbery) and internal issues (staff carelessness, abuse of assets).
- What statutes, requirements, or frameworks should we adhere to? Confirm the directive incorporates regulatory responsibilities such as GDPR, HIPAA, or sector-focused structures.
- How might situations get documented and addressed? Define straightforward methods for recognition, escalation, and reaction to lessen consequences once security incidents happen.
- How shall staff remain instructed and held liable? Determine approaches to deliver guidance, maintain continuous education, and apply standards consistently throughout the enterprise.
- How frequently must the directive undergo assessment and revision? Protection remains never fixed — guidelines should progress with evolving innovations, organizational shifts, and arising dangers.
7 Ways to Increase Organizational Security
Regular audits and testing
Ongoing protection assessments and intrusion checks remain vital for uncovering flaws within an enterprise’s framework. These inspections address aspects ranging from network barriers and permission mechanisms to program weaknesses and obsolete settings. Through replicating real-world intrusions, penetration evaluations expose ways an adversary might leverage openings in defenses. Consistent reviews further guarantee alignment with regulatory benchmarks including ISO 27001 or HIPAA. Once problems get detected, remedial actions should be recorded and monitored to achieve progress. Absent consistent examinations, weaknesses could stay hidden until targeted by hostile entities. In the end, evaluations deliver assurance that infrastructures are not merely protected today but resilient against developing challenges tomorrow.
Employee training
Workers frequently represent the primary barrier in defending against protection threats. A properly instructed team may detect fraudulent attempts, avoid harmful downloads, and react correctly to questionable behavior. Awareness initiatives for security must remain continuous, rather than restricted to single sessions, ensuring personnel remain informed about evolving dangers. Incorporating computer training programs into these initiatives strengthens employees’ ability to recognize risks and apply safe practices in real-world scenarios. Task-specific instruction guarantees staff comprehend the unique exposures tied to their duties. For instance, accounting departments should identify fraud schemes, whereas IT teams need to remain attentive to system intrusions. Instruction must additionally outline explicit escalation methods so staff understand where to report concerns. By minimizing human mistakes, enterprises significantly reduce their comprehensive threat posture.
On-premise deployment
Certain enterprises select on-premise installation of vital platforms to retain absolute authority regarding their information and frameworks. Compared with cloud-driven offerings, on-premise platforms enable companies to customize and apply individualized protection guidelines. This becomes especially significant in sectors such as healthcare, defense, or finance where delicate information must remain strictly protected. On-premise installation decreases dependence upon external vendors, lowering dangers linked to service disruptions or intrusions. It further permits enterprises to handle encryption credentials, recovery processes, and oversight internally. Nevertheless, it demands allocated assets for equipment, applications, and experienced personnel. For organizations possessing adequate capacity, on-premise installation can deliver exceptional safety and oversight.
Access control
Efficient entry management guarantees that staff members receive entry solely to the assets required within their functions. This concept of “least privilege” reduces the possible harm from internal risks or hijacked credentials. Entry management rules must incorporate robust verification techniques, including multi-factor checks (MFA), as well as network-level controls such as DNS filtering solutions that restrict access to malicious or unauthorized web destinations before connections are established. Position-oriented entry frameworks assist in maintaining permissions uniformly and lowering managerial effort. Frequent assessments remain necessary to revoke entry when staff alter positions or depart the organization. Observing entry records delivers transparency regarding abnormal or illegitimate actions. Through applying rigorous entry restrictions, enterprises enhance their complete defense stance and limit vulnerability against hazards.
Encryption
Encryption represents one among the strongest methods for safeguarding confidential information against unlawful entry. It guarantees that even when data becomes captured or stolen, it stays inaccessible without proper decoding keys. Information ought to remain encrypted both during transfer, for instance in email exchanges, encrypted video conferencing, and while stored, such as inside repositories or archival files. Robust encryption standards like AES-256 are regarded as industry-leading practice. Enterprises must further administer decryption keys safely to avoid abuse. Continuously refreshing encryption schemes aids in defending against shifting dangers. By rendering information indecipherable to outsiders, encryption maintains secrecy, reliability, and confidence.
Data hygiene
Proper information hygiene decreases exposure through restricting the volume of redundant or obsolete details an enterprise keeps. Retaining outdated documents, replicated entries, or disorganized information generates chances for intruders if those resources are not adequately safeguarded. A systematic method for information lifecycle oversight incorporates labeling, preservation, and secure elimination of details. Routine inspections assist in detecting information that is no longer essential for operational or legal reasons. Encoding or masking confidential information provides an extra shield of defense. Educating personnel about accountable information management remains equally vital. Through maintaining information hygiene, enterprises diminish their susceptibility to incidents and adhere more effectively to privacy requirements.
Establishing physical security
Physical protection is sometimes ignored, although it remains crucial for an enterprise’s complete defense. Unapproved physical entry into workplaces, server facilities, or information hubs may cause theft or harm to critical hardware. Safeguard mechanisms including monitoring cameras, badge entry, on-site badge printing, and patrol guards deliver visible prevention. Guest oversight platforms confirm that solely permitted persons may access limited zones. Tangible obstacles such as sealed enclosures and reinforced racks defend servers and storage units. Frequent inspections of barriers, alerts, and monitoring networks assist in sustaining preparedness. When integrated with digital safeguards, robust physical protection forms a comprehensive security strategy.
How Secure Is Your Business Communication?
Teams exchange sensitive information through video calls, messages, file sharing, and collaborative platforms. But how secure is this communication, and can you trust that your data is safe from unauthorized access?
Common Security Risks in Business Communication
- Data breaches from unsecured chat platforms or email.
- Eavesdropping on unencrypted video or voice calls.
- Phishing attacks targeting employees through communication apps.
- Compliance violations when tools do not meet industry security standards such as GDPR or HIPAA.
Without strong protection, conversations, documents, and client data may be exposed, leading to reputational and financial damage.
Why TrueConf Stands Out
TrueConf is designed with security-first principles, making it a reliable choice for organizations that prioritize confidentiality:
- End-to-end encryption secures all calls, messages, and data transfers.
- On-premise deployment ensures that data remains within the company’s infrastructure, not on third-party servers.
- Compliance-ready for industries such as healthcare, finance, and government where strict regulations apply.
- Granular access control allows administrators to manage permissions, authenticate users, and integrate with corporate security systems.
- Support for private corporate networks ensures communication remains fully under organizational control, even in offline environments.
Take your team communication to the next level with TrueConf!
A powerful self-hosted video conferencing solution for up to 1,000 users, available on desktop, mobile, and room systems.
Security Policy Templates
1. Information Security Policy Template
Purpose. This directive defines the enterprise’s method for safeguarding data resources from illegitimate entry, exposure, modification, or removal.
Scope. This directive extends to every staff member, partner, supplier, and platform that manages, stores, or transmits corporate information.
Policy:
- All confidential information shall be categorized and processed based on its degree of secrecy.
- Entry to information shall be provided under the principle of minimal privilege.
- Encryption shall be enforced for information while stored and during transfer.
- Periodic protection inspections shall be performed.
Responsibilities:
- Leadership guarantees that means are available for applying defense mechanisms.
- Technical personnel establish and oversee platforms consistent with this directive.
- Staff adhere to instructions and notify about protection events promptly.
Enforcement. Disregard of this directive could lead to corrective measures up to and including dismissal.
2. Acceptable Use Policy (AUP) Template
Purpose. Specify proper utilization of enterprise-owned technological assets.
Scope. Covers all individuals utilizing corporate equipment, systems, and programs.
Policy:
- Corporate equipment and systems are intended for organizational activities.
- Individuals shall not deploy unapproved applications or devices.
- Viewing unsuitable, unlawful, or harmful material is restricted.
- Distributing corporate information beyond permitted pathways is disallowed.
Responsibilities:
- Technical teams manage activity oversight mechanisms.
- Staff employ assets appropriately and disclose abuse.
Enforcement. Breaches could result in removal of access rights or corrective measures.
3. Incident Response Policy Template
Purpose. Describe how the enterprise intends to identify, react to, and restore after protection events.
Scope. Covers all personnel, platforms, and operational workflows.
Policy:
- Every staff member must notify suspected events without delay to the IT Security Group.
- Event handling procedures shall adhere to defined phases: identification, isolation, elimination, restoration, and after-action assessment.
- Communication with outside parties (customers, authorities) shall be directed through leadership.
Responsibilities:
- IT Security Group examines and resolves events.
- Staff assist with event handling activities.
Enforcement. Neglecting to follow notification protocols may result in corrective consequences.
4. Access Control Policy Template
Purpose. Guarantee appropriate entry into platforms and data.
Scope. Applies across all platforms, programs, and connections possessed or operated by the enterprise.
Policy:
- Individuals receive designated profiles with task-specific entry permissions.
- Multi-factor verification shall be required for critical platforms.
- Entry permissions shall undergo assessment every quarter.
- Departed staff accounts shall be deactivated within twenty-four hours.
Responsibilities:
- IT oversees and audits entry records.
- Supervisors authorize entry applications for their groups.
Enforcement. Any abuse of entry permissions could result in suspension or dismissal.
Conclusion
A successful protection framework depends upon more than tools—it requires well-defined, enforceable rules that direct conduct throughout the enterprise. The examples presented here were created to support establishing uniformity, lowering exposures, and encouraging responsibility.
Through tailoring such directives for each distinct environment and reassessing them frequently, the enterprise can reinforce its safeguards, enhance conformity, and cultivate a mindset of protection awareness. In the end, robust directives not merely defend information and resources but also preserve the confidence of staff, collaborators, and customers.
FAQ
What should a security policy include?
A protection directive needs to describe the objective, coverage, duties, accountabilities, proper usage, entry management, information safeguarding practices, and incident handling processes. It functions as a structure for defending resources and reinforcing responsibility.
Why is compliance important in security policy?
Adherence guarantees that an enterprise satisfies statutory, oversight, and sector requirements. This lessens responsibility, strengthens credibility, and assists in preventing expensive fines or image harm.
What is Bell-LaPadula security model?
The Bell-LaPadula framework emphasizes preserving information secrecy through blocking illegitimate exposure. It applies principles like “no read up, no write down” to regulate permissions.
What is Biba security model?
The Biba framework highlights information accuracy by guaranteeing details remain unmodified through illegitimate methods. Its guidelines involve “no write up, no read down” to maintain reliable information.
What is Clarke-Wilson security model?
The Clarke-Wilson framework enforces accuracy via properly structured operations and division of responsibilities. It depends upon verified users, regulated activities, and oversight to preserve reliable functions.
About the Author
Olga Afonina is a technology writer and industry expert specializing in video conferencing solutions and collaboration software. At TrueConf, she focuses on exploring the latest trends in collaboration technologies and providing businesses with practical insights into effective workplace communication. Drawing on her background in content development and industry research, Olga writes articles and reviews that help readers better understand the benefits of enterprise-grade communication.


Follow us on social networks