SSO (Single Sign-On) Explained: Why It Matters and What to Look For
What Is Single Sign-On (SSO)?
Picture starting each morning feeling frustrated, since remembering every login becomes overwhelming and leads to entering credentials again and again. This used to be a frequent challenge among many individuals and companies until Single Sign-On (SSO) arrived. SSO transformed this constant password burden into something simpler and far more effective.
Consider Jordan, for instance. A dedicated project coordinator, Jordan begins the day by entering one verified username and credential to unlock the organization’s core system. From there, it’s possible to view messages, interact with teammates, and operate digital platforms: without repeating the login process every time. That’s the benefit of SSO: it makes working across applications seamless and stress-free.
How Does Single Sign-On work?
Let’s explore the convenience of Single Sign-On (SSO), a method designed to simplify entry into multiple services. Through SSO, users enter just one set of credentials to gain access to numerous linked applications: no confusion, no repetitive logins. It’s like having one universal key that opens every digital lock you need.
When the initial login is complete, the system generates a secure token. This token works like a trusted signal, confirming the user’s identity. Typically stored safely, such as in a browser cookie, it informs all connected apps that the user is verified. The advantage of SSO is that there’s no need to type in a password repeatedly. As the user moves between apps, the token maintains access, saving effort and preventing login fatigue.
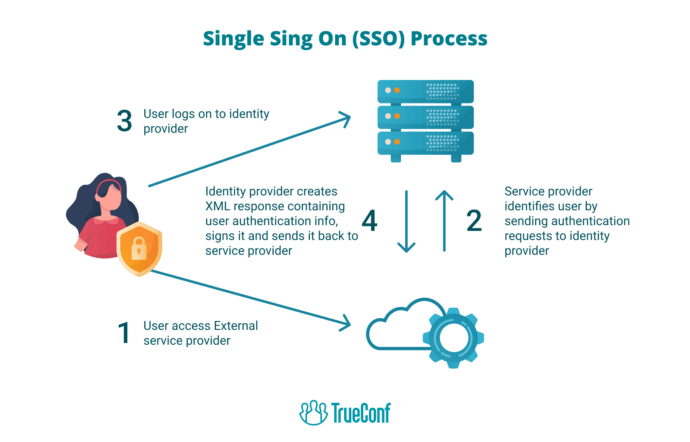
Types of Single Sign-On (SSO) Configurations
Several different methods exist to configure SSO, and each provides unique benefits. One example is Web-Based SSO, ideal when users rely on online platforms frequently. This setup allows seamless navigation between services using a single authentication step.
Next is Kerberos-Based SSO. This configuration implements advanced encryption to safeguard applications communicating across client-server environments. It works especially well within Windows-based networks and Active Directory frameworks.
Another approach is Federated Identity SSO. This model is well-suited for users from separate organizations who must interact with applications across domain boundaries. It proves highly valuable for enterprises needing secure resource sharing between partners.
Enterprise SSO fits well in large organizations with layered IT infrastructures. It addresses strict access control demands while simplifying how internal users authenticate across various tools.
Lastly, Social Login SSO enables access through third-party credentials like Google or Facebook. While convenient, it requires proper oversight to preserve data confidentiality and system integrity.
Every SSO type presents distinct strengths and weaknesses. Organizations must evaluate their architecture, required protections, and user preferences to select the most suitable solution.
What is an SSO Token?
Consider the moment when someone logs into the central platform that controls digital access. At that point, the system generates a unique SSO token assigned to the individual. This token holds details such as the user’s ID, login timestamp, and authorized areas. It’s encrypted for protection and follows the user, allowing smooth and secure navigation between various platforms.
What stands out about the token is its impact on the online experience. There’s no longer a need to recall countless credentials: a frustrating task when they’re forgotten. The SSO token simplifies access while enhancing safety. Many businesses rely on SSO tokens so that users can enter applications with minimal friction.
As one transitions across systems, the SSO token not only streamlines the process but also ensures ongoing protection. Think of it as a master key in a restricted archive—opening only for those with verified access. In this quiet yet essential role, the SSO token strengthens both connectivity and security in today’s connected environment.
Advantages and Disadvantages of Single Sign-On (SSO)
Advantages of Single Sign-On (SSO)
- Convenience: With Single Sign-On, users simply perform one login to reach multiple services. No repeated password recovery or delays involving help desks. Tools become instantly accessible upon sign-in, allowing work to begin without delay.
- Time-saving: After authentication, moving across platforms becomes fast and seamless. Entering credentials again is unnecessary, which saves effort and helps users stay engaged with important duties.
- Improved Security: Single Sign-On cuts down the number of required credentials, decreasing chances of weak or reused passwords. Additional protections, such as multi-step verification, can be included to block unauthorized access.
- Easier IT Management: For administrators, SSO streamlines identity oversight. Instead of juggling separate accounts, teams manage permissions through one system: improving control and minimizing unauthorized entry points.
Disadvantages of Single Sign-On (SSO)
- Risk of System Failure: If the central SSO system fails, user access across all platforms might be disrupted. This could halt operations until recovery, causing delays and productivity loss.
- Complex Setup: SSO implementation requires thorough coordination and advanced skills to integrate with existing environments. The configuration can be lengthy but typically results in lasting operational benefits.
- Dependence on External Providers: Should an SSO vendor encounter problems or cease service, access to key tools may be lost. This reliance brings potential risk if issues arise unexpectedly.
- Compatibility Issues: Certain legacy applications or niche platforms might not integrate with SSO solutions. Employees using these tools may still need separate logins, reducing overall consistency.
- Extra Security Steps: Though SSO is efficient, enhanced protections like two-step verification can slow down workflow slightly. These steps, while necessary, may feel burdensome when speed is a priority.
Social Login vs. Enterprise SSO
Social login enables individuals to access platforms by linking their existing Facebook or Google profiles. This method is quick and user-friendly, eliminating the process of generating new credentials or remembering extra passwords. As a result, social login works well for consumer-focused platforms where ease of entry is essential. Still, it raises privacy risks because personal account data from social networks is shared with external services. In addition, organizations have limited oversight over that information’s protection, making social login a weaker option for tools that process confidential materials.
Enterprise SSO, in contrast, caters to organizations prioritizing robust access and operational efficiency. Through Enterprise SSO, staff members unlock numerous internal tools with one secure login. This approach reduces password overload and simplifies user management for IT departments. Compared to social login, Enterprise SSO introduces better safeguards, such as multi-factor verification (MFA), to block unauthorized attempts. Although the setup demands more configuration and technical knowledge, it grants full authority over access protocols, making it the preferred model for enterprises with advanced security needs.
SSO Security Risks and How Secure It Is
While SSO improves login convenience, it also introduces vulnerabilities. Because SSO relies on one credential set across various systems, if a cybercriminal obtains a single login, they may gain entry to every connected service. This creates a centralized failure point. Phishing schemes are widespread — users may unknowingly provide their credentials, enabling intruders to breach multiple systems simultaneously.
In the absence of enhanced security controls, SSO might leave key systems at risk. A number of SSO configurations omit multi-factor authentication (MFA) by default, though MFA offers critical additional protection. If MFA is not implemented and a password is compromised, attackers can enter without further verification. Another threat is related to session handling — improperly managed session tokens may be exploited for unauthorized access.
Even with these concerns, when supported by proper safeguards like MFA and robust session regulation, SSO can offer high levels of security. It also minimizes password overload and enhances centralized access governance across systems.
What to Look for in an SSO Provider
Imagine walking through a vibrant marketplace, exploring options in search of the ideal Single Sign-On (SSO) provider. Every vendor stands prepared to highlight what sets them apart.
- Security First: Begin with the Security section. Here, vendors emphasize essentials like multi-factor protection and strong encryption: crucial elements for defending digital environments. One provider even highlights compliance with major frameworks such as GDPR and HIPAA, offering assurance through their strict adherence to industry regulations.
- Seamless Integration: Move on to the Integration zone, buzzing with various platform options. A standout provider may guarantee smooth compatibility with your current infrastructure, simplifying the process of linking existing apps to their SSO platform.
- User Experience: At the User Experience booth, vendors showcase intuitive designs. One live demonstration catches attention with its streamlined sign-in experience. The focus is on making login fast, minimizing friction, and improving user satisfaction.
- Scalability: In the Scalability corner, a vendor describes how their service adapts to company growth. Their promise: the ability to support rising numbers of users and applications as the organization expands.
- Customization Options: In the Customization area, vendors offer personalized adjustments. Features might include tailored branding and precise access permissions to fit unique organizational needs.
- Support and Reliability: At the Support and Reliability display, providers underline their dedicated assistance teams available around the clock. They ensure operational stability and promise dependable uptime.
- Cost Flexibility: Next is the Cost section, where vendors present various pricing structures. Options may range from per-user models to flat-rate plans, designed to accommodate different budget levels.
- Vendor Reputation: Before finishing the search, attention turns to Vendor Reputation. Reading through testimonials and feedback helps determine whether providers are dependable and well-regarded in the industry.

How Does SSO Compare with Other Access Management Solutions?
Before Single Sign-On (SSO) existed, users required unique credentials for individual applications: similar to needing a different boarding ticket for each leg of a journey. This process was inconvenient and increased risk if credentials were ever compromised.
SSO is more than a convenience tool: it also streamlines identity control. Picture it as a conductor guiding an orchestra from a central podium, coordinating access without confusion.
As organizations expand, adding employees and digital platforms can complicate control, like adding more instruments to a growing orchestra. SSO adapts efficiently, maintaining order while supporting scale.
Implementing SSO demands strategic preparation: similar to ensuring every section of an orchestra is tuned before a performance. Once implemented correctly, SSO integrates smoothly and generally requires less ongoing adjustment than other sophisticated access frameworks.
Ultimately, SSO offers a smart mix of simplicity and protection. Many enterprises pair it with multi-factor authentication (MFA) to enhance security while preserving ease of access. The most effective solution is always the one aligned with an organization’s operational requirements.
The Role of Active Directory in Single Sign-On (SSO)
Imagine operating in a workplace where every platform: email, task management solutions, and cloud drives, requires separate credentials. This often leads to forgotten passwords, resulting in delays and IT involvement to restore access. That’s where Active Directory (AD) becomes essential. Developed by Microsoft, AD enables users to sign in once and gain entry to all necessary tools. It eliminates the burden of password overload and keeps daily operations uninterrupted.
How Active Directory Powers SSO
One Sign-In for All Access
On her onboarding day, Lisa accesses her workstation using a single credential pair. In the background, Active Directory verifies her identity and grants unified access to essential tools: email, HR portals, and collaboration apps, without prompting her again. This is effortless for Lisa and a major efficiency boost for IT, allowing them to prioritize critical tasks.
A Central Hub for Identity Data
Picture AD as a vault securing all employee identity attributes, such as usernames, credentials, and group assignments. When Lisa tries to retrieve restricted content, AD checks her role-based permissions. If they align, she proceeds; if not, access is denied. This architecture guards sensitive assets and ensures strict access control.
Seamless Compatibility Across Systems
AD acts like an interpreter fluent in common access protocols such as Kerberos, LDAP, and SAML. When Lisa opens her email client, AD processes the request behind the scenes, authenticating her instantly: no repeated logins required, no interruptions.
Tailored Permissions for Every Role
Administrators configure AD to enforce access policies tailored to organizational structure. For instance, Lisa might be authorized to view project files but restricted from finance documents. This ensures that each employee can work efficiently without compromising sensitive data.
Security and Structure in One Place
Consolidating authentication through AD limits entry points for cyber threats. Fewer credentials mean fewer vulnerabilities. IT departments benefit from simplified monitoring and improved compliance documentation, thanks to centralized logs and standardized processes.
Anywhere Access with AD Federation Services
When the organization integrates cloud-based platforms, AD Federation Services (AD FS) maintains a consistent experience. Whether Lisa logs in from the office or remotely, she uses one credential set, ensuring continuity and security.
Scales with Organizational Growth
As companies expand, AD adjusts effortlessly. IT personnel can rapidly onboard users, assign access levels, and integrate new systems with minimal disruption. Its scalability and interoperability make it an ideal solution for businesses at any stage of development.
Why Companies Love Active Directory for SSO
For professionals like Lisa, Active Directory (AD) simplifies daily routines. A single login reduces delays and eliminates issues caused by misplaced credentials. For technical teams, it minimizes redundant efforts and manual resets. For organizations, AD offers an ideal balance of simplicity and protection, supporting productivity while maintaining data integrity.
Active Directory serves as more than just a software tool: it forms the foundation of streamlined operations, satisfied staff, and reliable cybersecurity. When paired with Single Sign-On (SSO), AD empowers businesses to create access systems that are secure, user-friendly, and built for scalability.

Follow us on social networks