# Users and groups. Integration with LDAP/Active Directory
Here are the minimum steps to obtain a functioning corporate communication system:
Select a machine (PC, physical or virtual server) with suitable hardware.
Configure HTTPS (it is used for many key features such as integration with the AI server, conference scheduling, etc.) and specify the external server address (guest page).
Configure server accessibility for users within the corporate network and, if necessary, from an external network (outside the CSPD).
Create user accounts or integrate the server with a directory service using the LDAP/LDAPS protocol. ◀️ You are here!
Install client applications for users and teach them how to connect to your server (see the desktop application documentation).
# User Accounts
In the User Accounts section you can add new user accounts, as well as edit and remote existing user accounts.
You cannot edit user details in LDAP mode. User data entry form is available only in Registry mode.
In TrueConf Server Free the number of user accounts is restricted. To learn more, go to the web page of this solution.
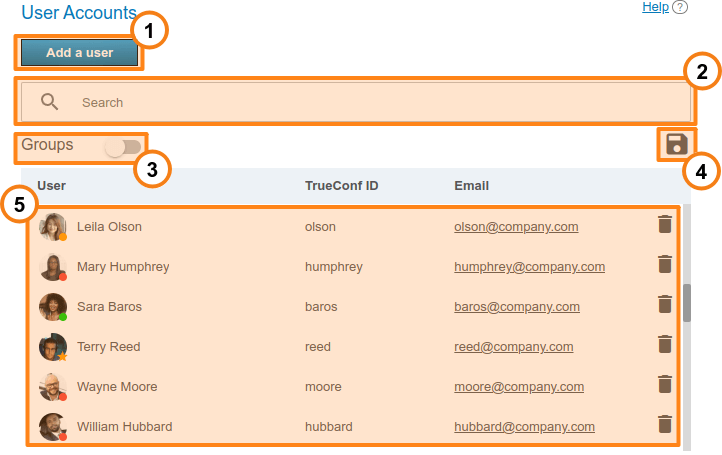
Add a new user.
Search users by TrueConf ID, first name, last name, display name, or email.
View user groups available on your TrueConf Server instance.
Export the list of users to a CSV file for later import to the address book of TrueConf Group (can be done in the Maintenance section of the endpoint control panel ). This button is available only in the Registry mode. The CSV file will saved in the UTF-8 encoding and ";" will be used as a separator which means that the preference settings will be ignored.
The list of the users registered on your TrueConf Server instance. At the bottom of each user's avatar, user status is displayed:
 — the user is online
— the user is online
 — the user is offline
— the user is offline
 — the user is in a conference or in a call
— the user is in a conference or in a call
 — the user is the owner in the conference
— the user is the owner in the conference
 — the user account is deactivated by the administrator (check the Status section in the profile).
— the user account is deactivated by the administrator (check the Status section in the profile).
Read how to connect users from outside your network to your TrueConf Server instance in our knowledge base.
In order to change user information, click on the username. To remove a user, click on the  button.
button.
# Endpoint authentication under the user's account
It is possible to register an SIP/H.323 endpoint on the server under a user’s account. This can give you several advantages when working with this endpoint:
Automatic export of the address book for the TrueConf Group endpoint (detailed configuration of this feature is described in the endpoint documentation)
Tracking the status of the endpoint as a regular user in the address book (online, busy, offline).
Please take into account that when each of the endpoints is authenticated, one online license is taken in addition to the gateway license (for more details, refer to the licensing section).
We do not recommend registering the endpoint on the same server using both SIP and H.323 protocols.
# User profile
If you create a user or click on any existing user in the list, you will be redirected to the page for entering or editing information about this person:
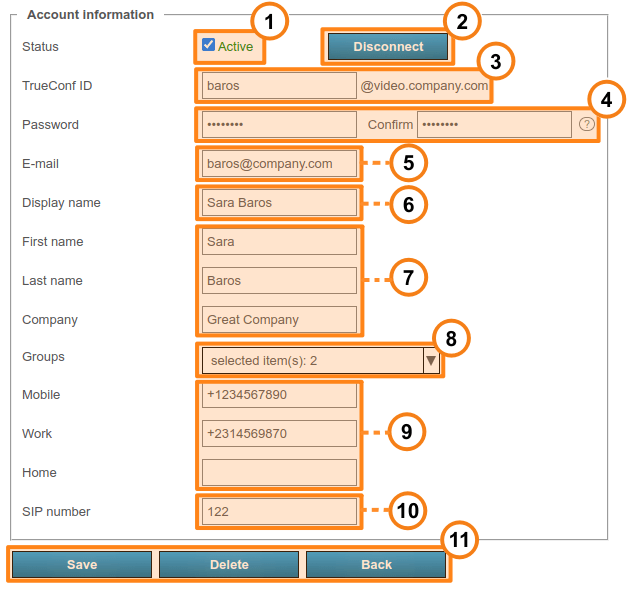
With the Active checkbox, you can change a user’s status to "active" or "inactive" (see below). Such users will be displayed semi-transparent in the general list with a grey status.
Use the Disconnect button to disconnect a user from TrueConf Server in all client applications. This feature may come in handy if you need to quickly connect a different user and the maximum number of connections is already reached (according to the license).
TrueConf ID is the unique identifier used for authentication in client applications and making calls. The user's login (the part of TrueConf ID before
@) can include only Latin and Cyrillic letters, digits, underscores, hyphens, and periods. The full TrueConf ID with the server name specified after the login (the extra part in the format@servernext to the input field) is needed for making calls to a user from a different server. The login is set when a user account is created and cannot be changed later.Enter the user's password. This password cannot be viewed when the account is created or edited, but it can be changed. Use the
 button which is next to the password confirmation field to view the password requirements.
button which is next to the password confirmation field to view the password requirements.Next, specify the email address that TrueConf Server will use to send notifications to the user via the associated SMTP server.
Display name is another required field which will be displayed in the address book of other users. This field is pre-filled with the username entered during Step 3. However, its value can be changed.
Next, comes a group of fields for various data about a user and his/her position in an organization. These fields are optional.
In the Groups drop-down list, you can add a user to the selected groups. Click on the arrow icon to view the list of groups available on the server. To add a user to one or more groups, just check the box to the left of a group name.
If necessary, you can enter the user’s phone numbers. One can call any of these numbers by clicking on it in the user profile section of TrueConf client application.
If SIP telephony is used, it is possible to specify a SIP call number in the corresponding field. If you do it, this field will be displayed in the user profile in TrueConf client application. When a user clicks on this field, the call will be started in the format
#sip:<number>. The number can be specified as<number>,sip:<number>or#sip:<number>.
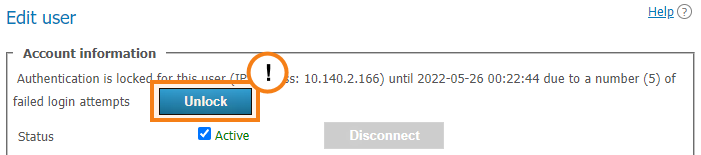
If a user has entered an incorrect password multiple times in a row (the exact number will be specified in the Users → Settings section), the authorizatin via the web application will be locked for 24 hours. You can enable the access to the application manually by clicking the Unlock button on the user profile page:
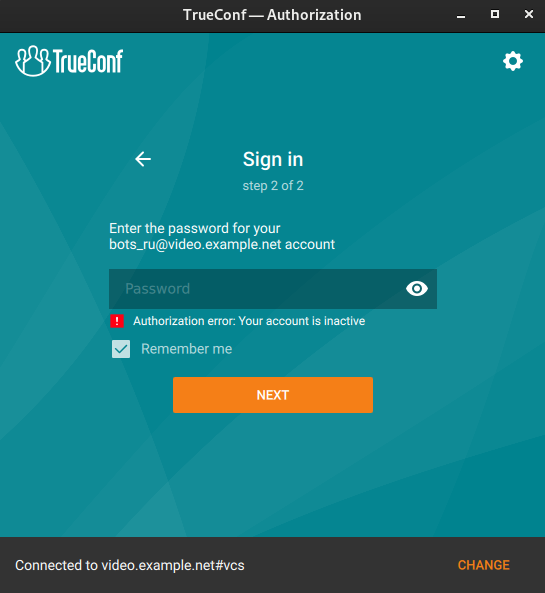
# User deactivation
The Active checkbox in a user’s account can determine if this user should be able to authorize. If the user account is inactive, it will not be deleted, but one will not be able to use it for authorization. The following message will be displayed in all client applications:
# Calls and conferences
If you are editing the user account created previously, you will see the Calls and conferences section where you can find the links for accessing:
Call history of the selected user
The general list of scheduled conferences and virtual rooms created on this server and filtered by this user. It will include only those meetings where this user is one of the participants.

The call history will include all user sessions in one-on-one calls and conferences:
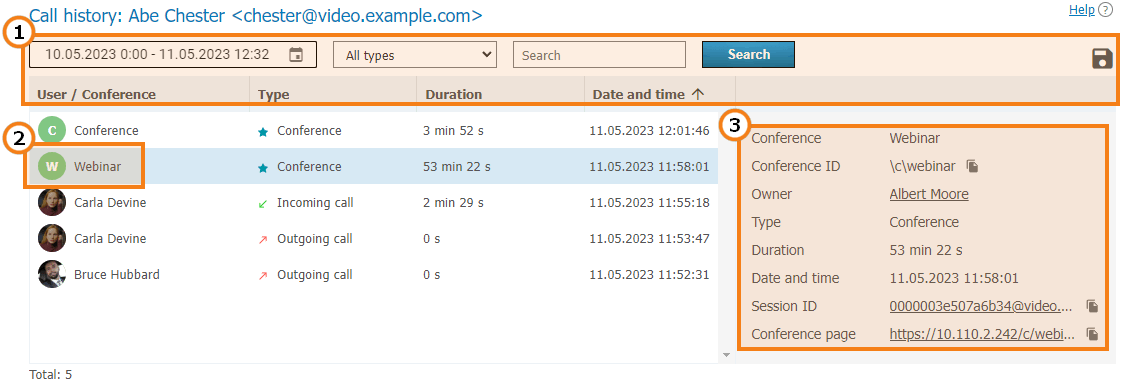
General UI for working with the table (check the description of the reports section). Events can be filtered by the following types:
All types (selected by default)
- Incoming call
- Outgoing call
- Missed call
Conference.
2. To view full information, select session (communication session) in the list on the left, Recurring conferences and virtual rooms may have multiple sessions depending on the number of times these conferences were started.
3. When selecting a session linked to the specific conference, you will see the following information in the card on the right:
Conference name and ID
The owner’s display name
Current session duration
Session start and end time
Link to the detailed information about the session in the Call history section
Link to the web page of a conference linked to the session. It will not be available for the meetings created ad hoc in TrueConf client applications.
# Application settings
On the page where a user account is either edited or created, the administrator can set special parameters that will be activated in the client application when a user authorizes on the server. These parameters can determine the restrictions for incoming and outgoing bitrate and can be found in the Application settings section.
If such settings have not been configured, group settings (if any) are applied to the user (the member of the group). User group settings are displayed next to the user settings field. They are displayed for preview only and cannot be changed. If a user is a member of multiple groups, the scope of the user rights will be defined by the group with fewer rights.
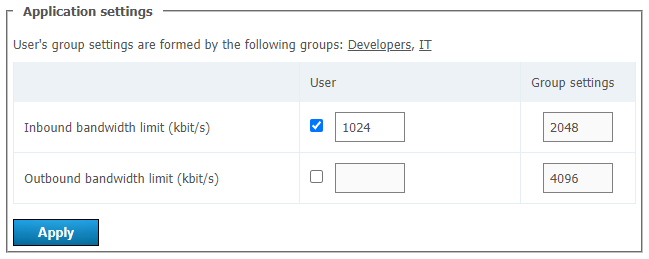
If bitrate restrictions are set at the user or group level, users will not be able to change them in TrueConf client applications, but will be able to see what parameters were selected.
User application settings have higher priority than group settings: if you put user restrictions lower than group restrictions, user restrictions will be applied.
# User address book
At the bottom of the page you can find the address book and edit buttons. The address book contains all the users who are located in the address books of the user groups where the user belongs.
You can add individual entries to the list, which will be displayed only to the user being edited. Please note that you can add not only TrueConf Server users, but any call string, such as conference ID, SIP/H.323 or RTSP in the address book. Subsequently, you can delete them using the  button. The user can delete them in the address book of the client application or in the personal area.
button. The user can delete them in the address book of the client application or in the personal area.
If address book editing is allowed at the group level, a user will be able to add contacts and organize them into groups in the client applications. Such groups are displayed only for the current user and are not included in the list of groups displayed in the control panel. However, the contacts added by the user will be displayed in the address book for his/her account in the control panel and the administrator will be able to edit this list.
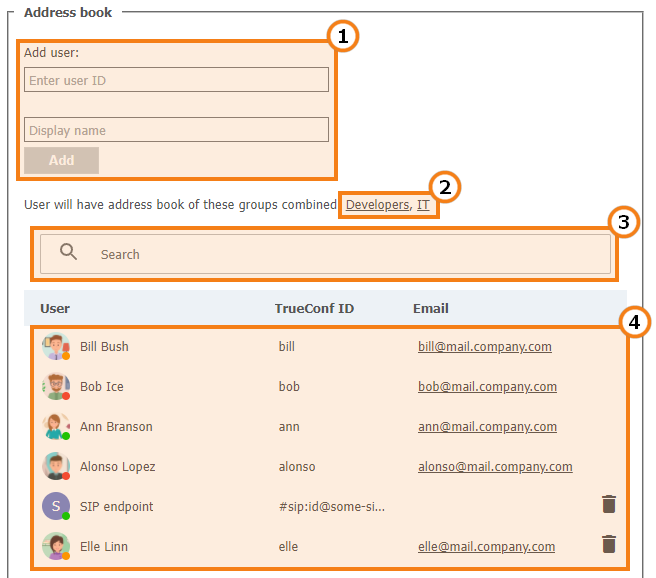
Add a user to the address book. To add a user, start typing the username or display name. From the drop-down list, select the user that matches your search (if the user is registered on your TrueConf Server instance).
The list of groups that the user belongs to, as well as the address books which are included in the user’s contact list and cannot be removed.
Search for users.
The list of users displayed in the address book. Click on the user registered on your TrueConf Server instance to edit their profile.
For examples of call strings that can be added to the address book, please refer to the user personal area documentation.
# Groups
In Groups tab you can create, rename, edit and delete groups. You can also add or remove users from the group, set up their address book and configure individual settings for the users of any group.
Manual editing of the user list and settings (e.g., group name) is not available in LDAP mode. You can only import groups from the LDAP directory as shown below.
Regardless of the data storage mode (Registry or LDAP), the following groups are included in the list by default:
Users without group — this group automatically includes the users who were not explicitly added to any group when their account was set or in this section as it will be described below.
Federated users — the users who make calls to the users or conferences on your TrueConf Server instance from a federated server.
Guest users — the guests who joined your public conferences (webinars).
It is impossible to rename or delete the default groups.
Each user group has specific permissions for using your video conferencing server.
# List of permissions for a user group
Please note that certain permissions cannot be given to the groups created by default. This restriction is set for security considerations (e.g., to make sure that operator rights are not available to everyone) and due to application logic reasons (e.g., since guests do not have a permanent account on your server, they cannot create conferences).
Below, there is the list of permissions that can be configured for user groups of TrueConf Server:












# Editing groups in Registry mode
Below, you can find an example of group settings for Registry mode, while some parameters will differ for LDAP mode.
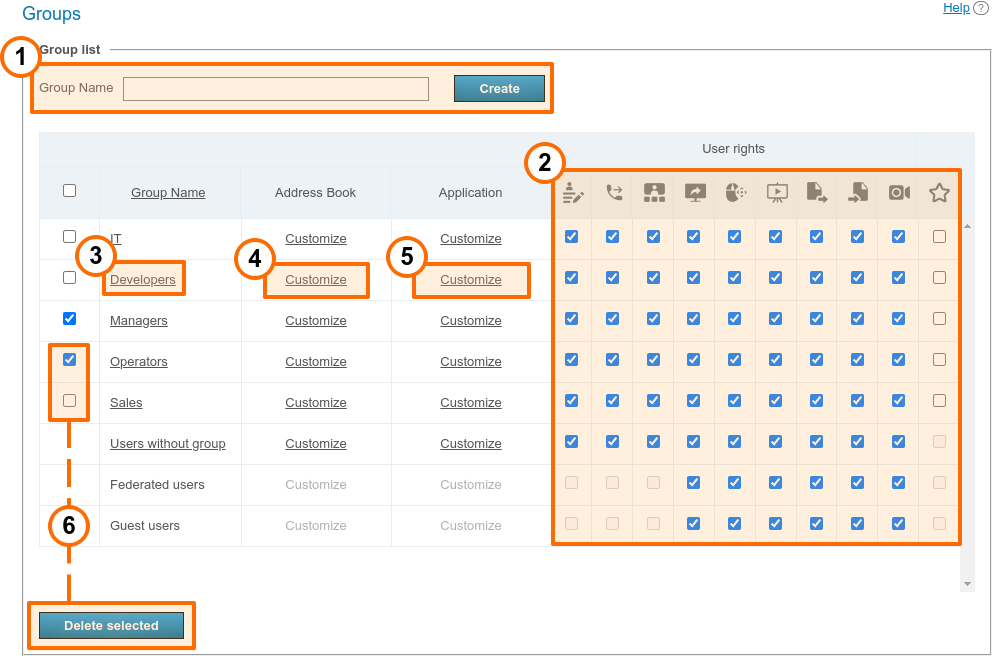
To add a new group, enter its name and press Create.
You can enable or disable certain features at the group level in the User rights section. These settings allow you to set different rights for users. The full list of these rights is provided above. Besides, read the description of how the rights work when a user belongs to several groups.
Click on the selected group in the list to open the menu where one can add or remove participants and change the group name. By clicking on the Group Name column, you can sort the list of groups alphabetically.
Click the Customize link in the Address Book column to create the contact list which would be the same for all group members.
Click the Customize link in the Application column to set up bandwidth limits for group participants.
The Customize link in the Group call pickup column allows you to configure group call pickup for the selected group.
To delete one or more groups, check corresponding boxes and click Delete selected. Accounts of the group members will not be deleted from your TrueConf Server instance.
# Configuration of group call pickup
The administrator can enable group calls for a user group. When this feature is activated, it will be possible to make calls to the entire group, rather than an individual user, so all group participants will see an incoming call. As soon as someone answers this call, it will be automatically declined for other users.
To enable group call pickup, click the Customize link in the Group call pickup column for the selected group in the general list.
On the opened page, you can configure the following settings:
The group for which settings should be configured (if necessary, you can quickly select a different group in the drop-down list).
The checkbox for enabling group call pickup.
Call ID which must be unique within the server. In other words, it cannot match other group call IDs and TrueConf ID of other user accounts. This ID should be used to start a group call. It can be added to the address book for future use. By default, it is identical to the group ID, but you can specify your own ID (e.g., a short string which is easier to use).
To save settings, don't forget to click the Apply button.
# Editing Groups in LDAP Mode
Manual editing of the user list and settings (e.g., group name) is not available in LDAP mode. You can only import groups from the LDAP directory as shown below.
If you would like to centrally manage user information and enable LDAP synchronization on your TrueConf Server instance, the list of users and groups is imported from the LDAP catalog (e.g., Active Directory). Note that your designated user search catalog object must contain all necessary user groups. For instance, if when configurating LDAP you indicated in the Group field the string cn=UsersGroup,ou=People,dc=example,dc=com, on the LDAP side the UsersGroup object must contain the necessary account groups:
In this case, system administrators will not be able to create user groups and add group members in the TrueConf Server control panel. Instead, they can be imported from the LDAP catalog. To do it, follow the next steps:
Open the TrueConf Server control panel and go to Users → Groups.
Click Change above the group list.
Enter your search and press
 . You can type both full group name or a keyword.
. You can type both full group name or a keyword.Click
 to add required groups to the list.
to add required groups to the list.Press Save to apply changes.
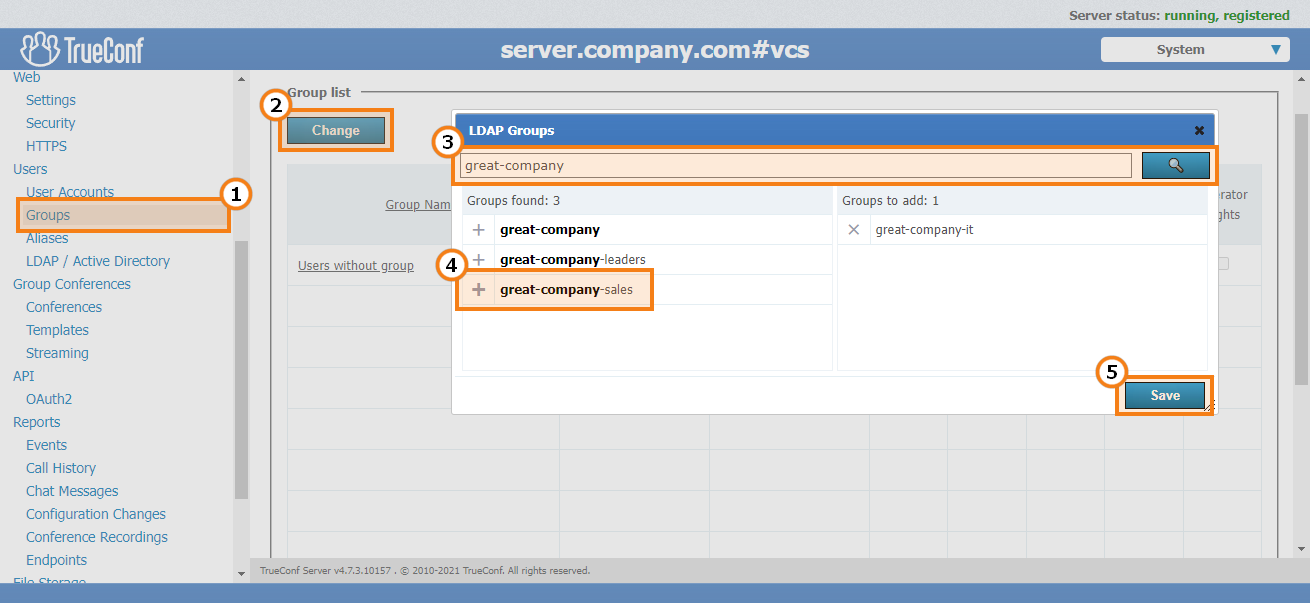
For groups imported from LDAP, just like in Registry mode, you can configure settings for user rights, address book, restrictions for client applications, and group call pickup.
# How the restrictions of rights work
If a user is a member of two groups: the permissive settings will override restrictive ones. For example, the user account is included in such groups as IT and DevOps. If the members of the IT group are allowed to show slides, the user will be allowed to show slides even if this feature is not permitted for the members of the DevOps group.
Group-level user rights can also be redefined by restrictions for authentication zones.
The persons who make a call to the users of your TrueConf Server via federation, will have the rights specified on your side (for the group Federated users) and on the side of their own server. For example, if you have disabled file sharing for federated users, they will not be able to send files when participating in the conferences hosted on your server, even if this right was given to them on their own TrueConf Server. Similarly, the federated user will be unable to send files if you have allowed this feature for federated users; but this right is denied to the group of this user on the side of his/her video conferencing server.
# Editing group's name and its members
Click on the group name from the list to access the User Accounts page. Here you can rename the group and edit the list of members using the corresponding buttons:
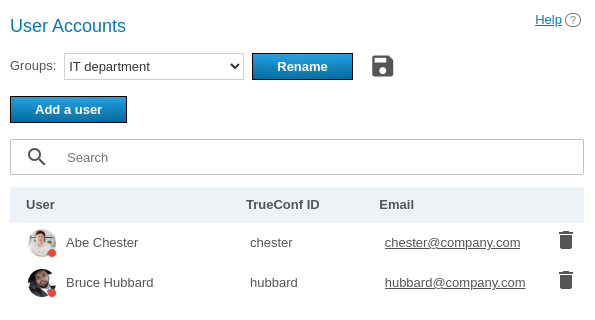
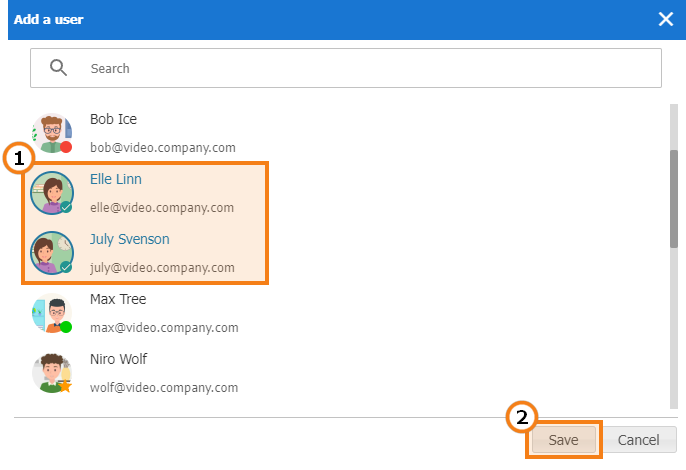
Click the Add a user button to complete the list. Select the users you want to add to the chosen group in the window. After that they will be marked with a checkmark. After all users have been selected, click Save:
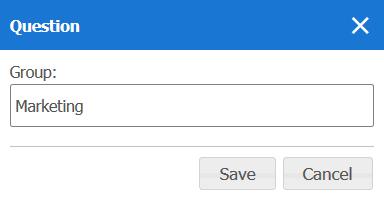
Click Rename to change the group name. Enter the new name and press Save (or press Cancel if you want to close the window without changing the settings):
You can also click the  button to export the user list of a specific group to a CSV file for subsequent import into the TrueConf Group address book.
button to export the user list of a specific group to a CSV file for subsequent import into the TrueConf Group address book.
# Setting up address book for users of the group
In the Address Book column of each group, click Customize. Click on it to edit the address book of this group. Group members can also add new contacts to the address book if they have a corresponding right (to enable it, please check Address Book Editing box).
You can add all users belonging to another group at once to the group’s address book (i. e. to the address book of each of its members). To that end, use Define, which users will be shown in the address book of the users in the group. Please note that automatic addition of users to the address book and manual addition are applied independently of each other.
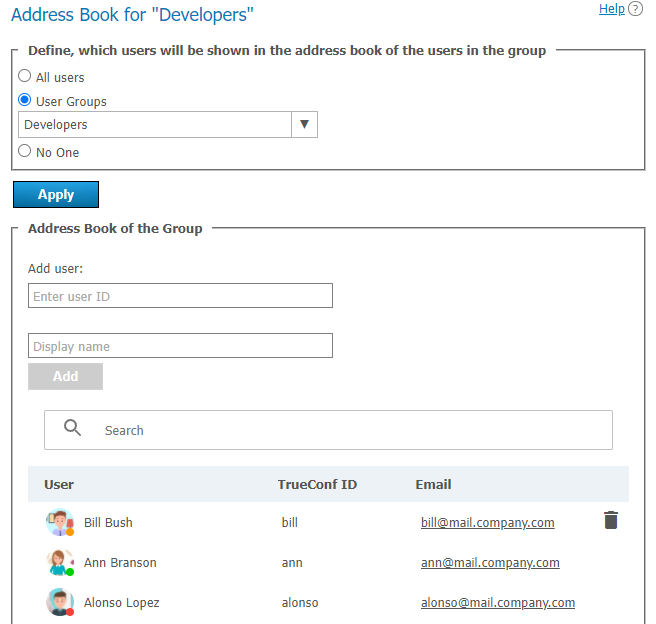
You can also manually add users of different types (this process is similar to adding users to the address book in the user's profile). However, group members cannot delete users themselves, because these contacts are added to the entire group and not to their personal address book.
Group members can search for other TrueConf Server users and add them to their list of contacts on their own (if you have enabled address book editing).
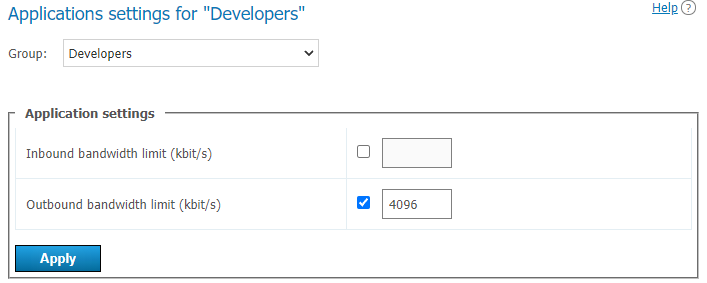
# Setting application settings for group users
Click Customize in Application column to set bandwidth limits for the group users.
# Aliases
# Description
Aliases allow you to find a contact by entering a short string (a kind of filter) instead of the full string. Such a contact can be:
A user from the same server
A user from a federated server
A call string via SIP, H.323, RTSP protocols (endpoint, IP camera, etc.)
A conference (including a conference held on a different server).
By adding an alias, you essentially create a new filter for quick searches in client applications. In the control panel, the administrator CANNOT use an alias as a full-fledged ID; for example, you cannot add an alias for a user or group in the address book.
This feature is especially useful when making calls to TrueConf Server from mobile devices with a digital keyboard. Shorter aliases help users to quickly find a contact or add it to the address book. The contact can be of any type which was mentioned previously.
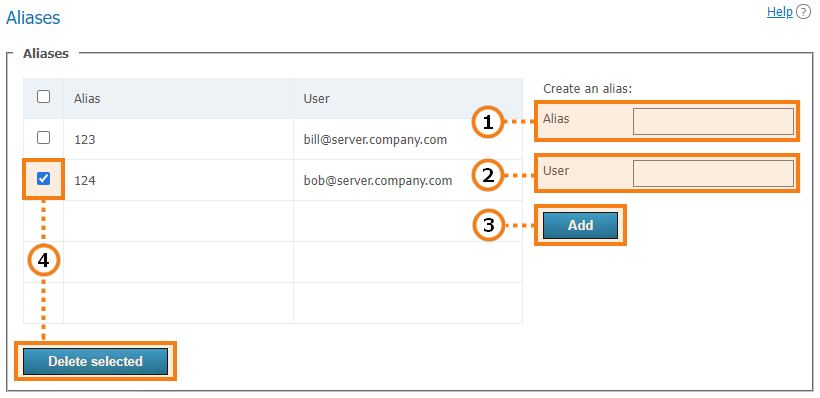
An alias may contain numbers, letters, hyphens
-and underscores_. The maximum number of characters is 32.Call string (including a server user’s login). Calls to this alias will be redirected to the user. To specify a conference, use the format
\c\ID@server.Press the button to add a new alias to the list.
To delete one or more aliases, mark them and click Delete selected.
Examples of call strings for alias configuration:
ceo_user— a user of your current server with the loginceo_userother_user@example.com— a user from a [federated server]](#alias-federation) with the addressexample.com\c\webinar— a conference on your current server. To copy the conference ID in this format, select the event in the general list and open the card of this event.\c\webinar@example.com— a conference held on a federated server with the addressexample.com#sip:@10.110.8.217— an SIP endpoint with the address10.110.8.217. If you need to call an endpoint registered on the server, when setting up the alias, you can specify the login of the user under which the endpoint is authenticated.
# Use for federation
In federation mode aliases can be used to make calls just like TrueConf ID. An alias will be resolved on the server which is specified after @ in the full alias@server alias , e.g., 122@video.server.name.
We will now discuss two examples of using aliases on federated TrueConf Server instances, one.name and two.name.
Case 1
Each of TrueConf Server instances has its own aliases. We have created an alias 111 for the user userA from the one.name server.
To make a call to userA from the two.name server, the following string should be entered in the address line:
111@server where server is the DNS name or IP address of the one.name server.
Case 2
Create an alias 111 on the two.name server for the user userA from the one.name server. It will correspond to the following call format:
userA@server where server is the DNS name or IP address of the one.name server.
In this case the users from the two.name server will be able to call users from the one.name server without its IP or DNS name. They will just have to enter aliases in the address line of their client application. For example, they can use 111 which we have discussed before.
The second option is more transparent for users, but in this case, it will be more difficult to configure a convenient system of aliases.
# Authentication
In this section you can configure authentication options for the users of your TrueConf Server.
Authentication may occur in two different security zones: trusted (or Trusted network as it is called by default) and external (untrusted) (called Internet by default). They are included from the very beginning and cannot be deleted. However, one can configure them as it will be described below.
Everyone, who does not get into the trusted zone, will automatically be moved to the external zone. A user’s IP address will determine the zone to which this person will belong.
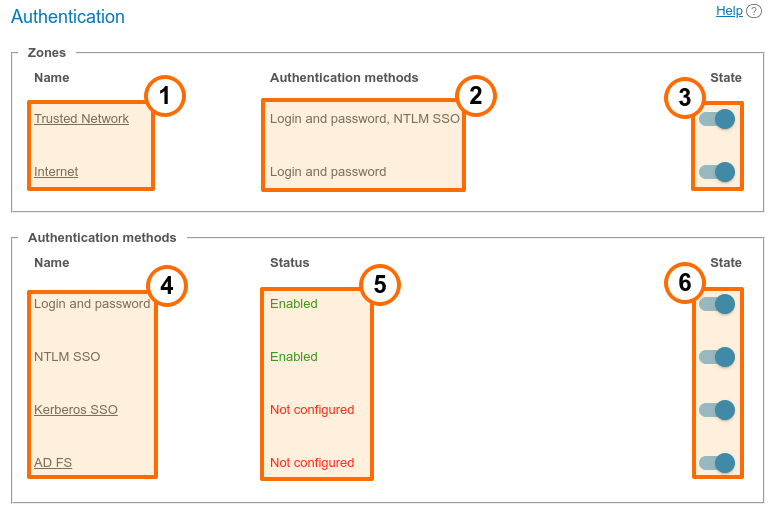
Security zones. To open the settings of the security zone, click on it.
Authentication methods specified for each zone.
Zone activation or deactivation. When a zone is deactivated, the users, who belong to this zone, will receive a notification that authorization is currently unavailable when they try to connect to your TrueConf Server. The users, who were connected previously, will be able to interact with the system up until the moment when the authorization token expires.
Authentication methods available for configuration. There are no parameters for Login and password and NTLM SSO options; they can be simply activated with switchers on the right side. To configure other authentication providers, click on their names.
The configuration and work status of each method.
Activation of authentication options.
Add two-factor authentication: AD FS (Active Directory Federation Services), Keycloak, manual settings for adding a different provider.
To enable Kerberos SSO and NTLM SSO methods, you have to select and configure LDAP account storage mode.
# Access zones settings
Click on the name of a trusted zone to open its settings:
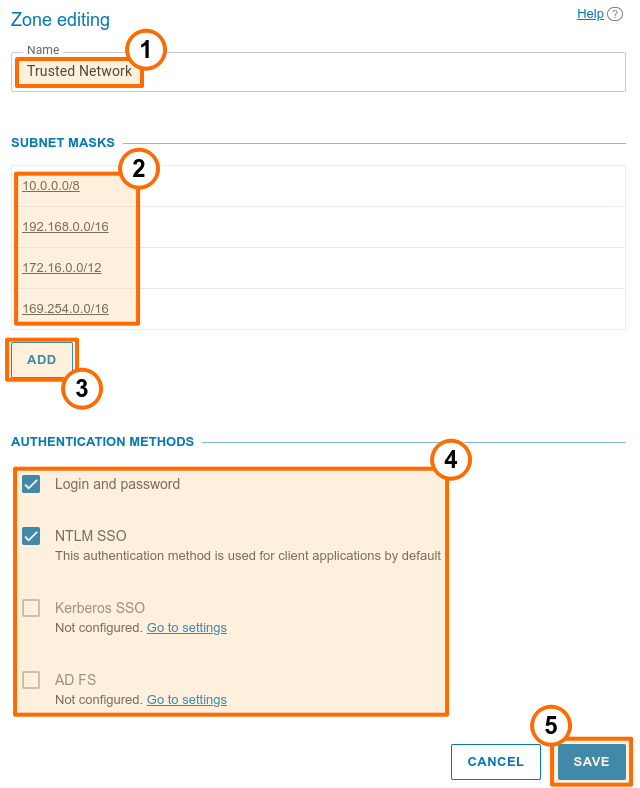
You can change the zone name, e.g., to “Corporate network”.
In the Subnet masks section, specify the network segments that are included in the current zone. By clicking on any entry, you will open the pop-up window for editing the address and subnet mask. Here, you can also delete the subnet. At least, one zone has to be specified for the trusted zone.
To add a new subnet to the list, click the Add button.
In the Authentication methods section, select required parameters by checking corresponding boxes. The list of zones is generated from the following options: login and password, NTLM SSO, Kerberos SSO, and other authentication providers which were added manually as shown below.
Below you can find the Available rights section, where one can select the rights available for each area. The list of available rights is the same as in the group settings, and restrictions will be added for selected groups which means:
The right is given to a user if he/she is in a zone where this right is allowed, and belongs to at least one group that was granted this right.
The right is denied to a user if he/she is in an area where this right is prohibited or belongs to groups that were not given this right.
Don’t forget to save changes to apply them on the server.
It is possible to specify the name of the external zone, its authentication methods, and available rights, but one cannot specify subnets.
# SSO settings
Single Sign-On (SSO) Technology, when integrated with an LDAP server, allows users of your TrueConf Server to authenticate automatically after logging into the OS on their PCs and launching their TrueConf client applications. To set up this feature, you can use one of the following options: Kerberos (opens new window), NTLM (opens new window), or Outlook SSO (when the server is run in integration with Microsoft Exchange Server).
To make sure that SSO authentication works correctly via NTLM, add the machine, where TrueConf Server is installed, and users’ PCs to the domain. In the case of Kerberos, only users’ PCs have to be registered in the domain, but this is not mandatory for the machine with TrueConf Server.
To activate NTLM you only need to enable this option in the State section; there are no additional settings.
To configure connection via Kerberos, click on the Kerberos SSO link in the Authentication methods section (on the Authentication page with the list of security zones):
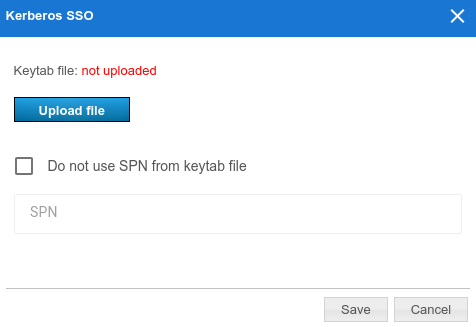
In the pop-up window, select:
The keytab file that will be used for authentication
If necessary, click on More and specify your own value for ServicePrincipalName (SPN) instead of the value saved in the file.
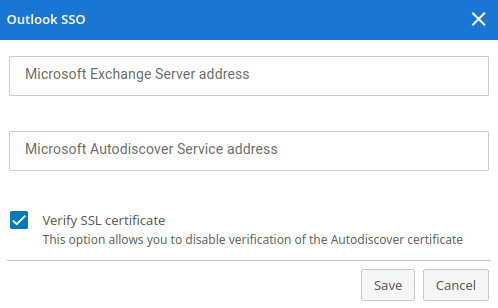
To configure SSO in the Outlook mail plugin, click on the Outlook SSO link. Specify the addresses in the pop-up window:
Microsoft Exchange Server host used for authentication token verification. It should follow this format:
{host}without specifying the protocol prefix (in other words, withouthttp/https)Microsoft Autodiscover Service host follows this format:
{host}without specifying the protocol prefix (in other words, withouthttp/https)Additionally, you can disable SSL certificate verification for the Autodiscover server.
# How to add two-factor (2FA) authentication providers
It is possible to add one or several methods of two-factor authentication (AD FS or OAuth 2.0 providers) to select them later for a certain zone(the number of providers is not limited). To do it, click Add in the Authentication methods section.
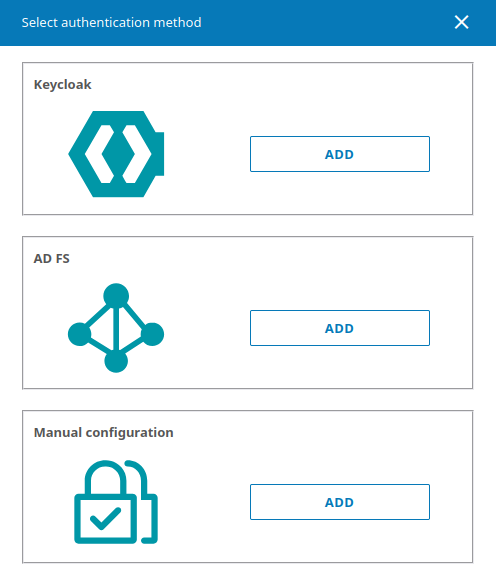
Active Directory Federation Services (AD FS) is the software component of Windows Server which acts as the authentication provider needed for accessing the resources outside the Active Directory corporate system, for example, it may be used for accessing web applications.
To configure integration with the selected authentication provider, click on the Add button in the corresponding section and specify the following parameters in the settings window:
The identifier (Client ID) of the OAuth application created on the side of AD FS for receiving the access token.
URI on the side of used for receiving the response from AD FS; it also needs to be specified on the federation service.
Authorization form URL on the provider's side.
Request token URL required for users' connection to TrueConf Server in case of successful authentication.
Logout URL.
Scope (Scope). Specify the
scopeselected when configuring the AD FS rule; for more details, refer to the Microsoft documentation (opens new window). You can specify multiple scopes by listing them separated by commas without spaces.The authentication provider name displayed in the list of authentication options on the page where access zones are configured and in TrueConf client applications when two-factor authentication is used.
On the side of TrueConf Server, you can also disable the verification of the SSL certificate received from AD FS.
To make it easier to distinguish one authentication method from another, you can set a custom image, by uploading it in the SVG format.
In addition to AD FS, other solutions may be used to implement two-factor authentication based on OAuth 2.0, for example, Keycloak. The list of settings will be identical to the settings for AD FS.
# LDAP / Active Directory
Switching between user data storage modes. TrueConf Server supports two types of data storage: Registry and LDAP. You can switch to any type by pressing Switch button:
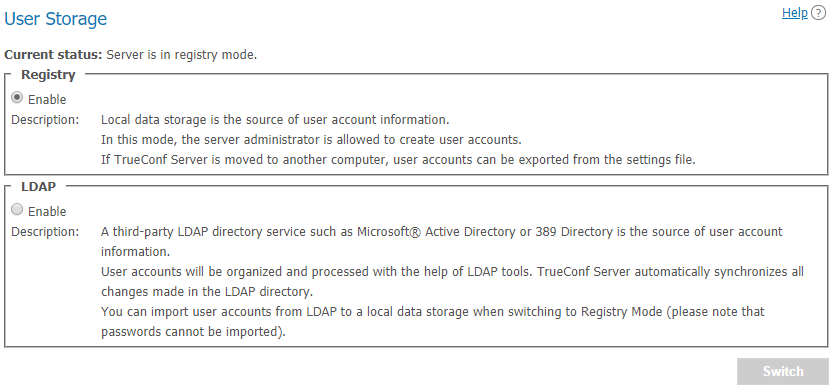
# Registry mode
Registry mode is used by default. In this mode, the server contains information about the users on the local server. You can add or remove users via control panel. If the server has been switched from Registry to LDAP data storage mode, existing user records will not be used anymore.
When switching to LDAP data storage mode, user records stored on the local computer will not be removed, so switching to another data storage mode will not damage saved information.
# LDAP mode
In this storage mode, the server takes user information from a remote or local LDAP directory. This approach offers a number of advantages when the server is used in the corporate environment:
Automatic syncing of user information
No need for authorization within the network at the workplace
Transparency, speed, and ease of administration
Administration security
Support for various directory services: Microsoft Active Directory, FreeIPA, OpenLDAP, 389 Directory Server, etc.
In LDAP mode you cannot edit user list and user group settings via control panel. By default, configuration settings for LDAP match Microsoft Active Directory. User information is edited using Active Directory management tools.
To learn more about the LDAP protocol and the Microsoft Active Directory service, read our website.
In LDAP mode, user rights correspond to the Active Directory group where users belong. To activate this mode, check LDAP → Enable and press LDAP settings button at the bottom. LDAP settings window will open:
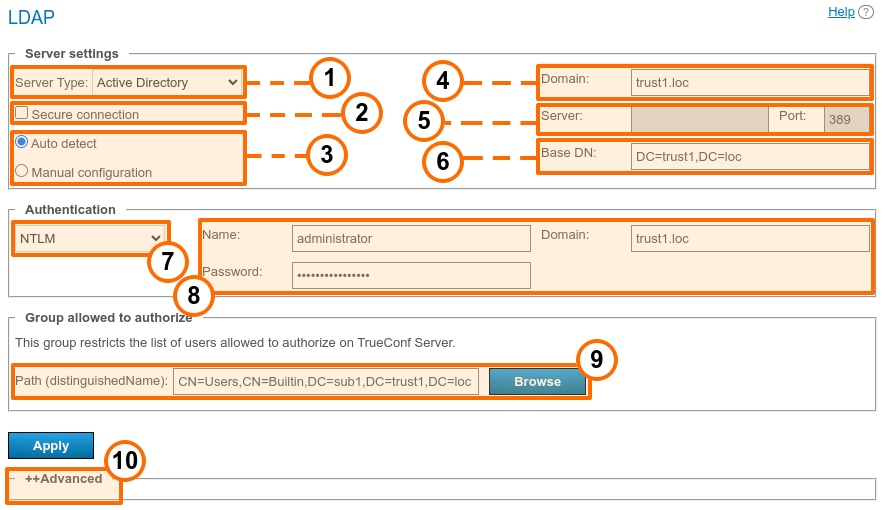
Supported server types: Active Directory, OpenLDAP, 389 Directory Server, FreeIPA. The default names of attributes read by the server from an LDAP directory will depend on this parameter. You can also select the Custom option to manually specify attribute names. After choosing the server type, to switch to its corresponding attribute names, expand the Advanced section below and click the Default button. You will see that the attribute names in the Value column have changed. If necessary, you can specify the required values and then click the Apply button in the Advanced section.
Connecting to the LDAP server in protected mode (via LDAPS protocol) to ensure secure transfer of user data over the network.
LDAP server settings configuration (automatic and manual).
In the automatic mode the LDAP server can be chosen among the servers by default of the DNS domain, specified in this field. Default servers are being chosen according to the relevant DNS-notes of SRV type. For Active Directory DNS domain name AD can be indicated here.
The address and port of the LDAP server when manual configuration is used. It is possible to use the global directory for connecting to the directory service. To do it, specify 3268 or *3269 as the connection port when working via LDAP and LDAPS respectively.
Base Distinguished Name is a directory object designed for searching users, e.g.
ou=People,dc=example,dc=com.TrueConf Server authorization modes on the LDAP server.
Authorization parameters on the LDAP server.
In this section, you can specify an LDAP group of users who will be allowed to authorize on TrueConf Server, for example,
cn=TC_Users,ou=People,dc=example,dc=com. It is possible to select a group by clicking on the Browse button. To enable this button, you need to fill out the fields required for connection to the LDAP server (in the Server settings and Authentication blocks) which will enable the Base DN field.Additional LDAP parameters. This will allow you to adjust the parameters to other types of LDAP servers.
Please note that if the server type is changed (for example, from Active Directory to OpenLDAP), the additional LDAP parameters are not automatically reset. To switch to the default parameter values for the new server, open the Advanced section and click the Default button.
When changing from LDAP mode to Registry mode it is possible to import user data. To do this, choose the Registry mode in the User storage tab, tick on Import User Information and click on Switch.
User passwords are not imported. After being imported the user accounts are inactive (see User accounts section).
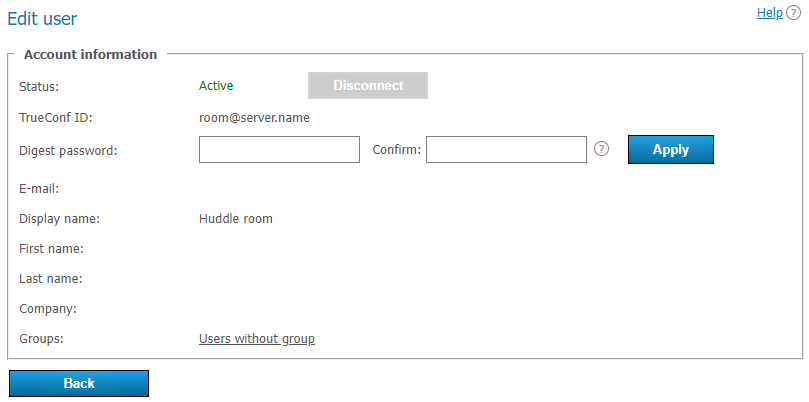
In LDAP mode, only the digest password will be available for editing in the user profile. This digest password must be specified when registering an SIP/H.323 endpoint on TrueConf Server. The same password should be specified in the authorization settings for the endpoint:
Directory of groups and users registered on TrueConf Server. This tab allows to create and manage the user’s groups. User Accounts tabs allows creating groups and managing rights. In the Registry mode a user can belong to one (or more) created groups. This parameter can be edited in the edit user information window. In the LDAP mode this window allows you to define rights for several LDAP groups. User attribute can be defined in the LDAP folder.
To import user groups from LDAP, open Users → Groups. Click the Change button and select corresponding groups in the drop-down list. Read more in our article on how to set up user groups.
When groups of users are imported from LDAP, the list will include only the groups that are included in it by default.
If you have several TrueConf Server instances connected to a common LDAP directory, users can log in to the personal area from a guest page of any of the connected servers. In addition, users can participate in private meetings hosted on a different TrueConf Server instance connected to a common LDAP directory using an auto-generated login.
# Additional LDAP parameters
Below you can find additional LDAP parameters and their purpose (user fields, filter rules, etc.). Depending on the chosen provider type, some parameters may contain pre-filled values (which can be reset if necessary):
Login — login
Display Name — full display name
First Name — first name
Middle Name — middle name / patronymic
Last Name — last name
Email — email
Company — the name of the organization
Branch — the name of the branch office
Department — department
Job Title — job position
Manager — the manager's name
Address — user's address
Max Results — the total number of pages returned in the search results (5000 is selected by default for all templates of LDAP providers)
Max Request Limit — the number of pages returned by a single request (1000 is selected for all templates by default). This means the server requests data from the LDAP directory in batches of this many pages until it reaches the limit set in Max Results
Filter Disabled — (for Active Directory only) determines whether the user is included or not
Group Member — determines which participants are in a specific group
memberOf — (for Active Directory only) the parameter which is responsible for linking an object to groups. It includes the list of group DN entries for each user (needed for filtering users by groups).
Filter Login — the filter for searching by logins
Filter CallID — not used, retained for backward compatibility
Filter Group — the filter for searching by groups which prevents other objects with matching names from being loaded
Attr primaryGroupId — (for Active Directory only) group ID parameter
Attr primaryGroupToken — (for Active Directory only) group token parameter
Attr objectSid — (for Active Directory only) object ID parameter
Attr SIP Phone — the SIP number for calling the user
Mobile Phone — mobile phone number for contacting the user
Work Phone — work phone number for contacting the user
Home Phone — a home (personal) phone number for contacting the user
User Status Attr — the attribute that determines the user's absence status across different servers simultaneously
User ID Attr — the attribute that determines the user's absence status across different servers simultaneously by his/her ID
Full ID Attr — the attribute that determines the user’s absence status across different servers simultaneously with the help of the full user ID (with the domain name included)
DetailedUserInfo Attribute — overrides the fields that will be displayed in the user information
User Alias List — the list of attributes that will serve as user aliases after authorization
TrustPartner Attr — (for Active Directory only) the filter that enables you to combine multiple domains into a trusted domain
FlatName Attr — (for Active Directory only) the display name for the trusted domain, when multiple domains are combined into a trusted domain
TrustedDomain Filter — (for Active Directory only) the filter that allows you to combine multiple domains into a trusted domain
ForeignSecurityPrincipal Filter — (only for Active Directory) the filter that allows you to combine multiple domains into a trusted domain
Trust Enabled — (for Active Directory only) the filter that allows you to combine multiple domains into a trusted domain
FilterClientSearchByLoginGroup — (
boolean) used for searching contacts in a client application. If this attribute is not specified explicitly, it defaults totrue. Moreover, only the users who belong to the login group will be found. If set tofalse, it allows finding other users in the LDAP directory who, for some reason, are NOT yet part of the login group.Use Avatars — has to be set to
1to make sure that avatars are loaded correctly in applicationsAllow Avatar Propagating — has to be set to
1to make sure that avatars are loaded correctly in applicationsAddressBook Refresh — a timer (in seconds) for periodic caching of relationships between groups and regeneration of address books. When the timer expires, it is assumed that the request did not yield any search results.
Filter AddressBook — the filter that can be used to create a user's address book
TimeOut — the time allowed for connection/request execution (in seconds). When this time elapses, it is assumed that the request did not yield any search results.
thumbnailPhoto Attr — avatar
jpegPhoto Attr — storage location for the avatar
Meeting Room Filter is the filter for getting the list of conference venues (such as meeting rooms), used together with Meeting Room Search Filter Attr
Meeting Room Search Filter Attr is an LDAP attribute that contains the conference venues
Meeting Room BaseDN — not used
LDAP Login with subdomain — allow users from subdomains to sign in, their login will be in the format
sub.domain\user.
# How to upload user accounts from different domains
Create a group with the area of application (range) Domain Local on the main domain to which TrueConf Server will be connected.
Move to this group the accounts of users (or user groups with the universal range; nested groups are supported only within a single forest) that you want to upload on the server.
Complete the steps 1 and 2 for all domains that will be used for uploading accounts.
Specify this group in the field Path (distinguishedName) in LDAP settings.
Make sure that the parameter Trust Enabled in LDAP settings is equal to 1 (default value) in the Advanced section.
# Certificate installation for LDAPS connection
To ensure connection via LDAPS, one may have to upload the root SSL certificate on the physical or virtual machine where TrueConf Server is deployed. This certificate should correspond to the domain where the domain controller server operates. To do it, copy the root SSL certificate of the domain to any directory on the machine with TrueConf Server.
Please note that the certificate has to be in the .crt format. So, if a different format is used, you will need to convert the certificate as it is described in this article.
Next, install the .crt certificate depending on your OS:
For Windows OS
Double-click on the certificate.
Click on the Install Certificate button in the certificate installation window.
Select Local Machine in the pop-up where the storage location has to be specified.
Select Place all certificates in the following storage and click Browse in the storage settings window that will be displayed next.
In the list of storages, select Trusted Root Certification Authorities and click OK.
To complete configuration, click the Next and Finish buttons.
Debian:
- Run the following command in the terminal as the administrator:
cp /home/$USER/cert.crt /usr/local/share/ca-certificates && update-ca-certificates
where /home/$USER/cert.crt is the absolute path to the .crt certificate copied to the machine with TrueConf Server.
2. Please reboot the computer on which TrueConf Server is installed.
CentOS:
- Run the following command in the terminal as the administrator:
cp /home/$USER/cert.crt /etc/pki/ca-trust/source/anchors/ && update-ca-trust
where /home/$USER/cert.crt is the absolute path to the .crt certificate copied to the machine with TrueConf Server.
2. Please reboot the computer on which TrueConf Server is installed.
# How to address typical issues when using LDAP
When LDAP is configured, some errors may occur while connecting to the directory service. In such cases, after you click on the Apply button which is in the connection parameters block, the corresponding notification will be displayed in the upper part of the screen. Below you can find some typical issues:
LDAP error 81 (Server Down)
No connection with the directory service. Most likely, TrueConf Server cannot access this service via the specified address and TCP port (389 for the standard connection and 636 for the secure connection via LDAPS). To test the connection, you can use the console application telnet (available on Windows and Linux):
telnet [ldap-server] [port]
where [ldap-server] is the address while [port] is the port of the server that acts as the domain controller. For example, if you need to test access via LDAPS, you need to run:
telnet ldap.example.com 636
If there is no connection, it is necessary to check the network equipment settings or network-to-network software. One should also make sure that the server acting as the domain controller has been started.
LDAP error 49 (Invalid Credentials)
Unable to authorize on the LDAP server. Make sure to provide the correct service account data used for connection to the directory service (go to LDAP settings, the Authentication section).
LDAP error -1
This error may occur when connecting to the directory service via the secure LDAPS connection. This problem may occur due to various reasons.
- It is necessary to make sure that the root SSL certificate of the domain, which includes the domain controller server, is uploaded on the physical or virtual machine where TrueConf Server is deployed. When the certificate is uploaded, you can test the connection with the openssl program: run the following command in a Windows or Linux terminal:
openssl s_client -connect [ldap-server]:[port]
where [ldap-server] is the address while [port] is the port of the server acting as the domain controller.
2. If TrueConf Server is deployed on Linux, and connection to Microsoft Active Directory has to be configured, make sure to specify the fully qualified domain name (FQDN) of the machine, where the domain controller server is deployed, in the Domain field. It should include the name of this machine, for example, server-name.ldap.example.com. In this case, FQDN should be used in the command testing SSL connection (check the previous step).
Connection has been established, but the list of accounts is empty
Make sure that the set of filters in the Advanced tab corresponds to the selected server type (Active Directory, OpenLDAP, 389 Directory Server). To switch to the corresponding attribute name after the server type is changed, click the Default button and configure required filters.
The users from the main domain are displayed, but the users from trusted domains are missing
Make sure that:
The Trust Enabled parameter equals 1 in the Advanced section, LDAP settings.
The account used for connecting to the domain controller server has the right to read the attribute member of from the container ForeignSecurityPrincipals.
# Password and account lockout settings
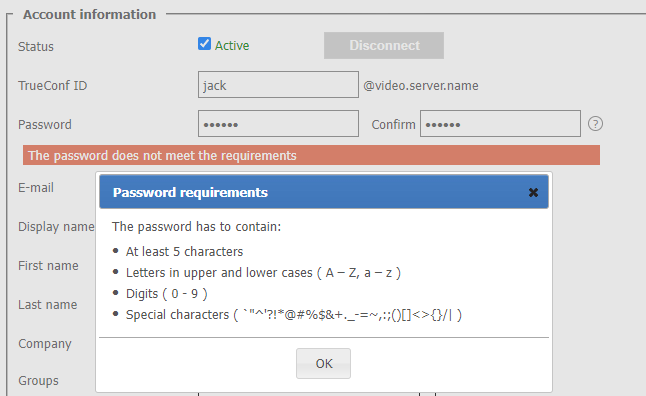
# Password requirements
If Registry mode is used, in the Password requirements section, you can specify the minimum allowable password length (from 2 to 64) and select mandatory characters (upper and lower case letters, numbers, special characters) for users of your TrueConf Server. A password will be checked against these requirements when a new account is added or when the password is changed for an existing account. This includes the cases when a user edits the password in the personal area:
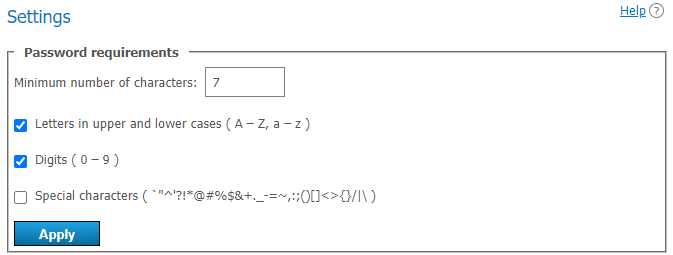
If the password does not meet the requirements, an error message will be displayed. Click on the ![]() button (which is next to the input field) to view the password requirements:
button (which is next to the input field) to view the password requirements:
# Automatic lockout
In the Account lockout policy section, you can configure the logic for locking a user account in the event of incorrect password entry during authentication.
Lockout settings are available both in Registry and LDAP modes. The lockout should be configured on the side of the video conferencing server; it is not related to AD/LDAP settings.
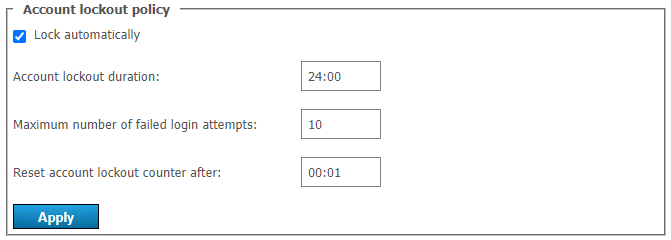
Here, you can specify:
account lockout period (a user can be manually unlocked at any time in his/her profile)
maximum number of failed login attempts
time interval between unsuccessful login attempts (if the interval is larger than the specified value, the counter for unsuccessful login attempts will be reset to zero).
Let us consider the following example. Here, we will use these settings:
Account lockout duration = 6:00 (6 hours);
Maximum number of failed login attempts = 5;
Reset account lockout counter after = 00:10 (10 minutes).
If a user with an existing server login (TrueConf ID) makes five failed attempts to enter a password with less than 10 minutes between each attempt, the account will be locked for 6 hours. However, if there is a 10-minute gap after any attempt (e.g., after the 4th attempt), the counter will be reset to 1.
# Display of fields from a user card
In the Displaying fields section, you can select which user profile fields will be visible in the following parts of the UI:
When opening a contact card (information about another user) in the application or in the personal area
(Has to be configured separately) when user information is viewed by the users from a federated server.
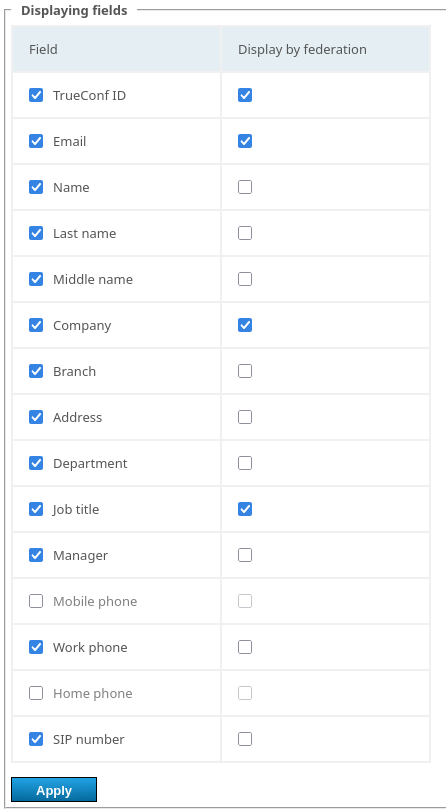
In the Field column, select which user data from your TrueConf Server will be available to anyone. In the Display by federation column, specify which of the selected fields will be shared with federated users who view information about the users of your server.
After completing user setup, you can install client applications for them and teach them how to connect to your server (see the desktop application documentation). This will conclude the essential steps necessary to launch the TrueConf corporate messenger with video conferencing!