TrueConf Server के साथ एकीकरण
Expand the capabilities of your solution through integration with a range of external devices, services, and platforms, ensuring seamless compatibility for various use cases.

Expand the capabilities of your solution through integration with a range of external devices, services, and platforms, ensuring seamless compatibility for various use cases.
and other Chromium-based ones
and others that support the iCalendar standard
and others that support the ICAP protocol
and others that support the LDAP protocol
TrueConf AI Server
एक कृत्रिम बुद्धिमत्ता-आधारित कॉन्फ़्रेंस ट्रांसक्रिप्शन सर्वर कॉर्पोरेट नेटवर्क के भीतर सुरक्षित डेटा प्रोसेसिंग की गारंटी देता है।
TrueConf Calendar Connector
TrueConf Calendar Connector provides simple and seamless integration between Microsoft® Exchange and TrueConf Server. View Outlook events in TrueConf client applications and schedule video conferences directly from your email calendar!
TrueConf Chatbot Connector
Develop multifunctional chatbots to automate workflows and integrate them into your TrueConf corporate communications, enhancing efficiency and improving the quality of team collaboration.
Maintain continuity and efficiency in communication, working both in compact meeting rooms and large conference halls, thanks to the seamless integration of TrueConf video conferencing solutions.
Enterprise-grade mail solutions like Microsoft Exchange or Communigate Systems provide organizations with a secure, scalable, and unified communication framework. These platforms deliver advanced email management capabilities, including intelligent routing, archiving, retention policies, spam filtering, and high-availability configurations that support large volumes of corporate communication.
In addition to shared calendars, contacts, and collaborative scheduling tools, they implement robust security mechanisms such as encryption, authentication controls, data-loss prevention, and threat protection. Their centralized administration functions enable IT teams to manage users, permissions, storage, and system monitoring from a single interface, significantly reducing operational complexity and enhancing productivity across the organization.
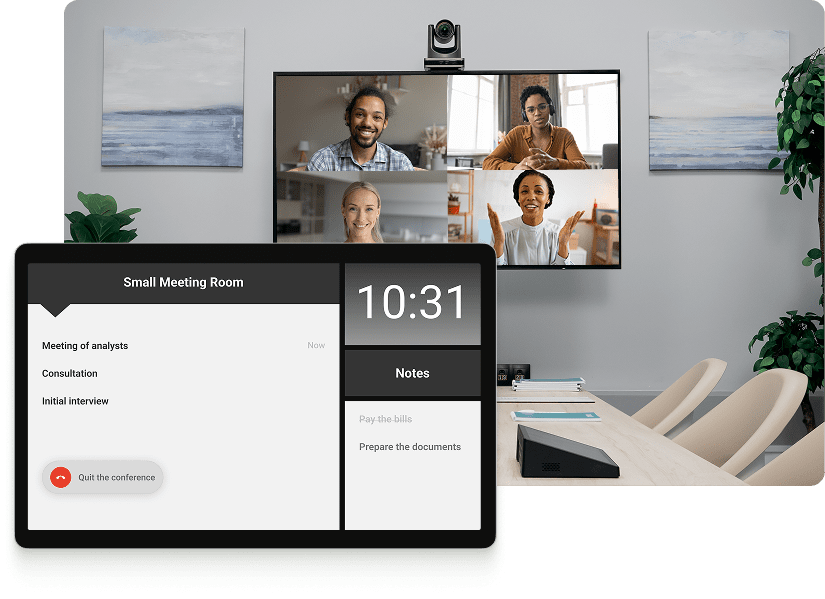
Hardware video conferencing endpoints are specialized devices engineered to deliver high-quality audio and video communication in meeting rooms, classrooms, and corporate settings. Unlike software-based clients that rely on a computer or mobile device, these endpoints incorporate dedicated processing modules, professional-grade cameras, speakerphones, and network components to ensure stable performance, low latency, and reliable media transmission.
They are widely deployed in boardrooms, huddle rooms, telemedicine suites, and remote collaboration environments where consistent quality and ease of management are essential. Leading manufacturers include Cisco, Yealink, Poly, HUAWEI, AVer, Avaya, and Grandstream: brands recognized for producing standards-based SIP/H.323 endpoints, wide-angle cameras, PTZ equipment, noise reduction technology, and integration capabilities with third-party conferencing platforms. Many endpoints also include features such as content sharing, multi-screen layouts, encryption, device management tools, and interoperability with cloud meeting services.
RTSP/RTMP protocols facilitate low-latency live streaming, enabling organizations to broadcast events, webinars, or announcements to a broad audience. These protocols are engineered for real-time media delivery, ensuring stable performance even in environments with fluctuating network conditions.
By streaming through RTSP or RTMP, organizations can distribute high-quality audio and video content to major platforms that support large-scale live broadcasts. This method enables real-time engagement, broadens audience reach beyond internal systems, and provides seamless access for viewers without requiring specialized applications. Additionally, compatibility with established streaming platforms ensures reliable distribution, adaptive playback, and support for both public and private streaming scenarios.
Learning management platforms provide tools for course creation, assessments, user tracking, and remote education at scale. As centralized online environments, LMS systems allow educators and organizations to create structured learning paths, deliver instructional resources, and evaluate learner outcomes through quizzes, assignment tasks, and interactive activities.
Moodle and comparable systems support asynchronous and synchronous learning formats, enabling students to access content easily, collaborate with peers, and communicate with instructors. They also provide administrative features including enrollment management, reporting, grading workflows, and integration with external tools and content libraries. By streamlining these operations, LMS platforms enhance accessibility, reduce administrative workload, and establish a consistent, scalable framework for online education and professional development.
These protocols allow users to authenticate once and gain access to multiple systems securely, reducing friction and enhancing access control. SSO technologies streamline the login workflow by delegating authentication to a trusted identity provider, which verifies user credentials and issues tokens or tickets that other services can validate.
NTLM and Kerberos are commonly deployed in Windows-based enterprise environments, where Kerberos provides ticket-based authentication with strong cryptographic protection, and NTLM operates as a fallback mechanism for legacy systems. OpenID Connect, built on top of OAuth 2.0, enables secure authentication for web and cloud applications through standardized identity tokens and API-driven verification. Together, these technologies simplify identity management, reinforce security, and deliver a smooth user experience across distributed applications and services.
MFA adds an additional verification layer beyond passwords, significantly reducing unauthorized access risks. By requiring users to present two or more independent authentication factors, such as something they know (password), something they possess (a mobile device or token), or something they are (biometric data): MFA substantially strengthens identity assurance.
Traditional password-only systems are vulnerable to phishing, credential theft, brute-force attempts, and password reuse across services. MFA counters these vulnerabilities by ensuring that compromised credentials alone are not sufficient to access an account. As cyberattacks become more sophisticated, organizations across many industries adopt MFA/2FA to enhance security compliance, safeguard sensitive data, and maintain a resilient authentication framework for employees, customers, and partners.
APIs and SDKs enable developers to build custom solutions, automate workflows, extend platform functionality, and incorporate communication or data features into their applications. These tools provide standardized interfaces that allow software to interact with external systems, databases, authentication services, and third-party applications.
Through APIs, developers can programmatically access platform capabilities, such as managing users, retrieving analytics, sending notifications, triggering operations, or synchronizing information across environments. SDKs complement this by offering prebuilt libraries, utilities, and documentation that simplify complex tasks like authentication, real-time communication, media processing, or device control.
Together, APIs and SDKs significantly accelerate development cycles, reduce implementation overhead, and make it easier to create scalable, interoperable solutions that integrate smoothly into existing infrastructures. They empower teams to deliver richer user experiences, automate business processes, and innovate more rapidly on top of modern digital ecosystems.