# Description
The all-in-one TrueConf Enterprise solution includes the TrueConf Border Controller extension that provides external users (outside the corporate network environment) with secure access to video conferencing servers.
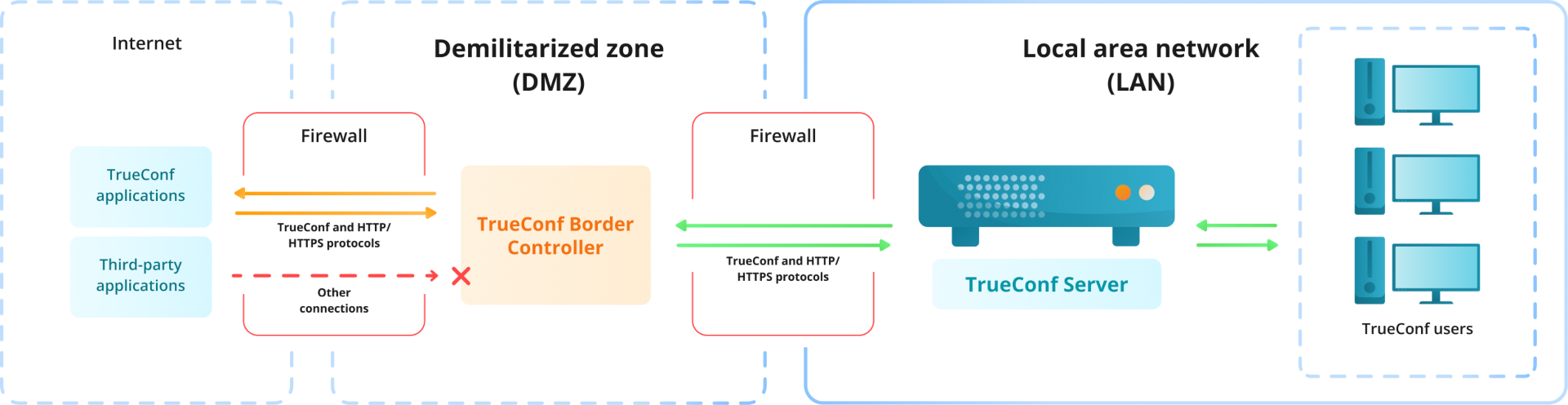
TrueConf Border Controller is a separate extension that acts as a border controller designed to be installed in the DMZ (demilitarized zone) of the corporate network and allowing only secure traffic from TrueConf client applications.
# Parts of the solution
The extension includes two components, which validate traffic according to TrueConf and HTTP/HTTPS protocols, respectively.
We recommend using HTTPS on TrueConf Server since it improves the security of the web server resources and ensures the work of the scheduler, real-time meeting management tool, browser-based conference participation and access to a user’s personal area.
Each TrueConf Border Controller component is configured separately and operates independently; so, you can configure only the TrueConf traffic to pass, but not HTTPS.
How TrueConf Border Controller works:
# How the solution works
The TrueConf Border Controller extension is installed in the DMZ.
The extension checks the protocol of traffic incoming from external networks. In other words, users specify the address of the machine with TrueConf Border Controller instead of the target server in their TrueConf application or browser. This conceals the actual address of the video conferencing server(s) and filters out unnecessary traffic.
If traffic is not sent via TrueConf or HTTPS protocols, it will be discarded.
If the extension detects traffic from TrueConf applications or the traffic sent via HTTPS, it is accepted, and a new connection is established from TrueConf Border Controller to the specified TrueConf Server or TrueConf Enterprise. When the connection is established, packets received from the application are sent via the new connection to the video conferencing server, allowing traffic over TrueConf and HTTPS protocols. This mechanism does not only ensure media stream transmission, but also enables the work of the scheduler, provides access to the web pages of the video conferencing server, supports federation, and more.
If necessary, the traffic from TrueConf Border Controller to the video conferencing server can be encrypted with the help of multiple symmetric algorithms, including PSK (Pre-Shared Key) (opens new window).
Apart from encryption, the extension does not perform any additional operations on traffic like analysis, saving, transfer to third-party services, and so forth.
So, the protection of a video conferencing server installed inside the corporate network is based on the following principles:
TrueConf Border Controller does not create a new connection to TrueConf Server until it determines that the packets are coming from TrueConf client application or via the secure HTTPS protocol.
No external traffic is directed to the video conferencing server by TrueConf Border Controller. This includes the traffic via SIP/H.323/RTP and others. For example, only TrueConf client applications will be able to connect to TrueConf Server from outside the network.
The IP address of the video conferencing server inside the corporate network is hidden. The server only has to be connected to the DMZ, but it does not have to be connected to the Internet. Please note that server federation will be impossible if there is no connection with the Internet.
Additionally, it is possible to encrypt the traffic transmitted via the TrueConf protocol.
Every component of the extension is an executable file that does not require installation. It can be run from the console or added as a service on Windows or daemon on Linux.